AWS Concepts ¶
Availability Zone 🌐¶
An Availability Zone is a single data center or a group of data centers within a Region. Availability Zones are located tens of miles apart from each other. This is close enough to have low latency (the time between when content requested and received) between Availability Zones. However, if a disaster occurs in one part of the Region, they are distant enough to reduce the chance that multiple Availability Zones are affected.
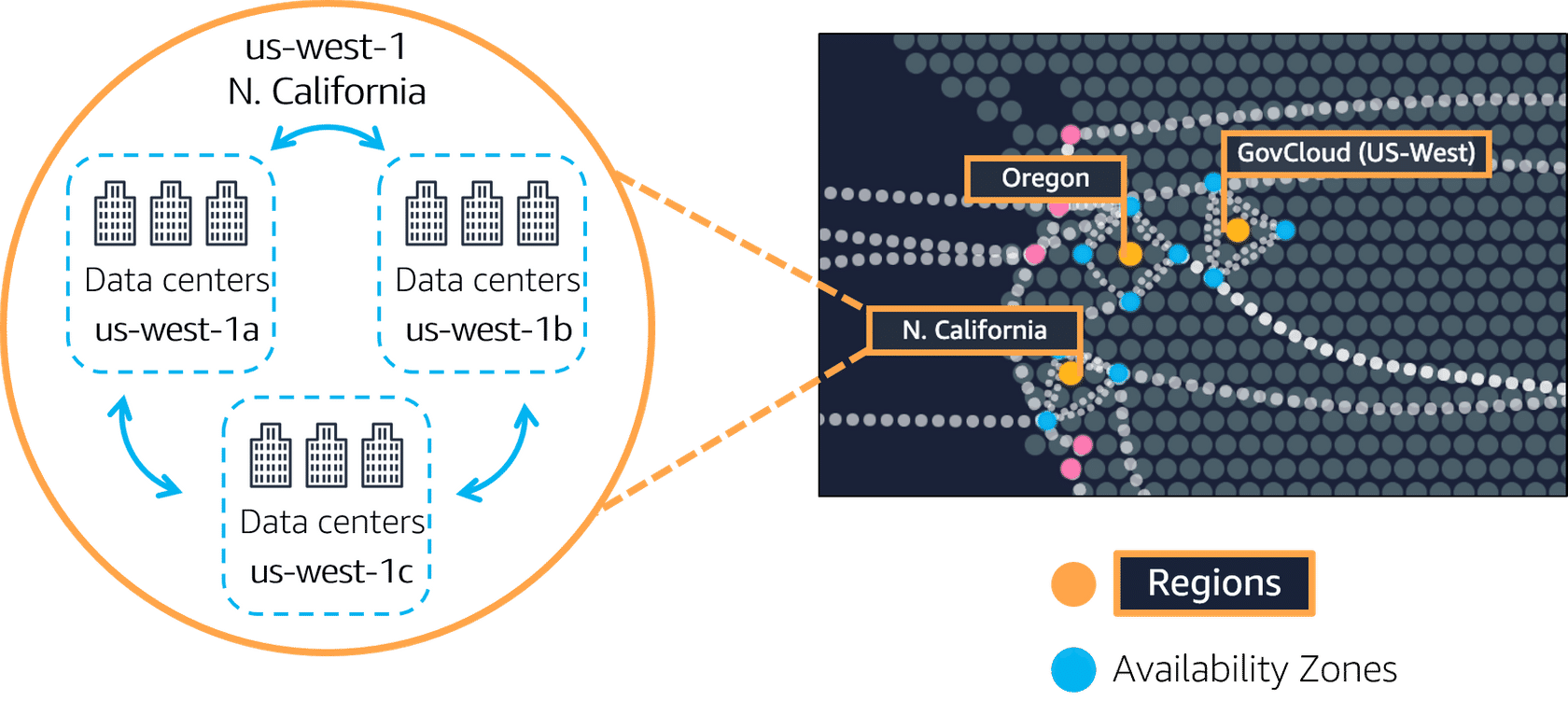
Each AZ will always have at least one other AZ that is geographically located within the same area, usually a city, linked by highly resilient and very low latency private fiber-optic connections. However, each AZ will be isolated from the others using separate power and network connectivity that minimizes impact to other AZs should a single AZ fail.
These low latency links between AZs are used by many AWS services to replicate data for high availability and resilience purposes.
Example
When RDS (Relational Database Service) is configured for ‘Multi-AZ’ deployments, AWS will use synchronous replication between its primary and secondary database and asynchronous replication for any read replicas that have been created.
Often, there are three, four, or even five AZs linked together via these low latency connections. This localized geographical grouping of multiple AZs, which would include multiple data centers, is defined as an AWS Region
Naming for AZ's
Availability Zones are always referenced by their Code Name, which is defined by the AZs Region Code Name that the AZ belongs to, followed by a letter. For example, the AZs within the eu-west-1 region (EU Ireland), are:
- eu-west-1a
- eu-west-1b
- eu-west-1c
Region 🌎¶
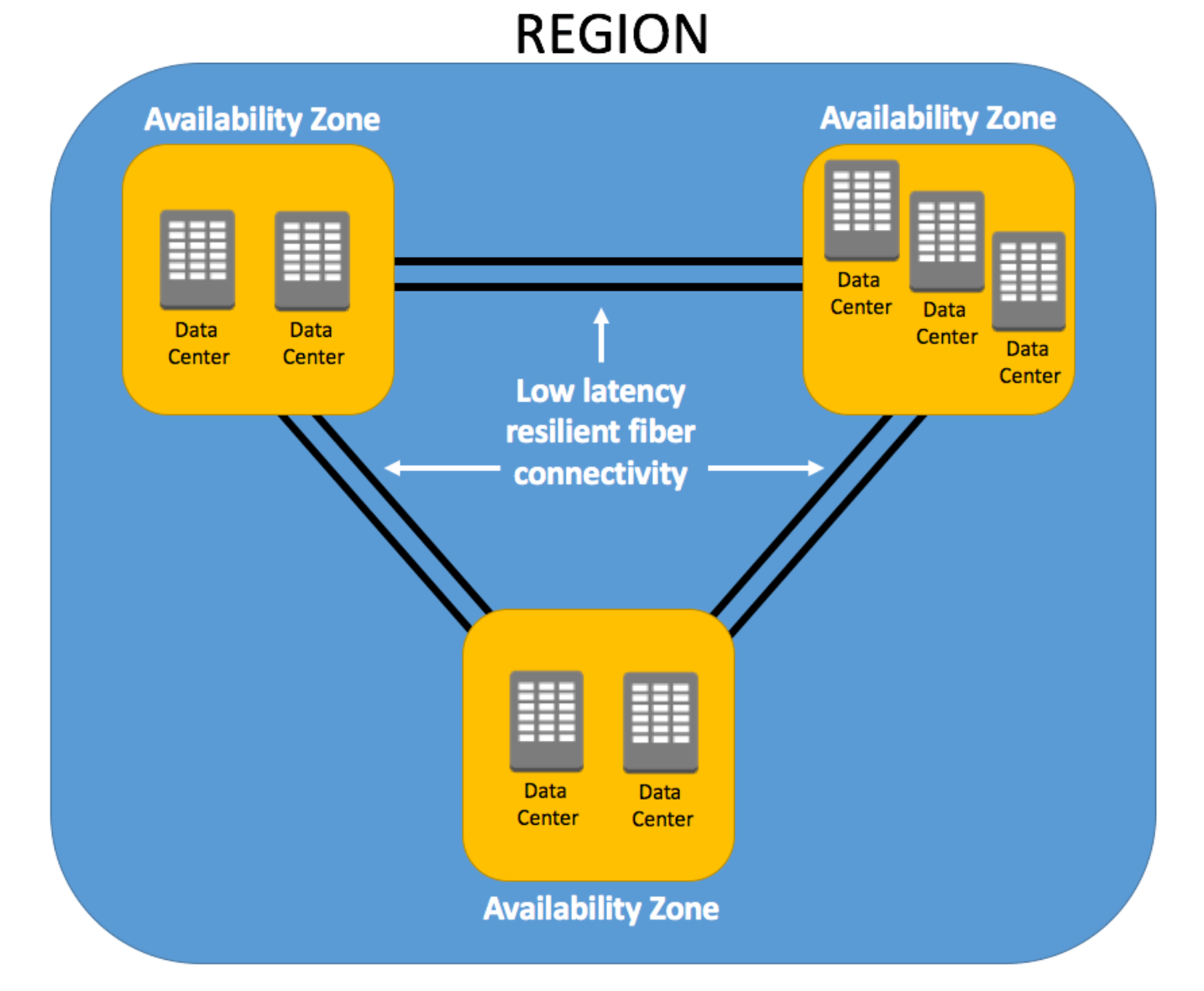
Multiple AZs within a region allows you to create highly available and resilient applications and services. By architecting your solutions to utilize resources across more than one AZ ensures that minimal or no impact will occur to your infrastructure should an AZ experience a failure, which does happen.
Having global regions also allows for compliance with regulations, laws, and governance relating to data storage (at rest and in transit). For example, you may be required to keep all data within a specific location, such as Europe. Having multiple regions within this location allows an organization to meet this requirement.
Edge Locations 📲¶
Edge Locations are AWS sites deployed in major cities and highly populated areas across the globe. They far outnumber the number of availability zones available.
While Edge Locations are not used to deploy your main infrastructures such as EC2 instances, EBS storage, VPCs, or RDS resources like AZs, they are used by AWS services such as AWS CloudFront and AWS Lambda@Edge (currently in Preview) to cache data and reduce latency for end-user access by using the Edge Locations as a global Content Delivery Network (CDN).
As a result, Edge Locations are primarily usedby end users who are accessing and using your services.
Example
You may have your website hosted on EC2 instances and S3 (your origin) within the Ohio region with a configured CloudFront distribution associated. When a user accesses your website from Europe, they would be re-directed to their closest Edge Location (in Europe) where cached data could be read on your website, significantly reducing latency.
Regional Edge Cache 📦¶
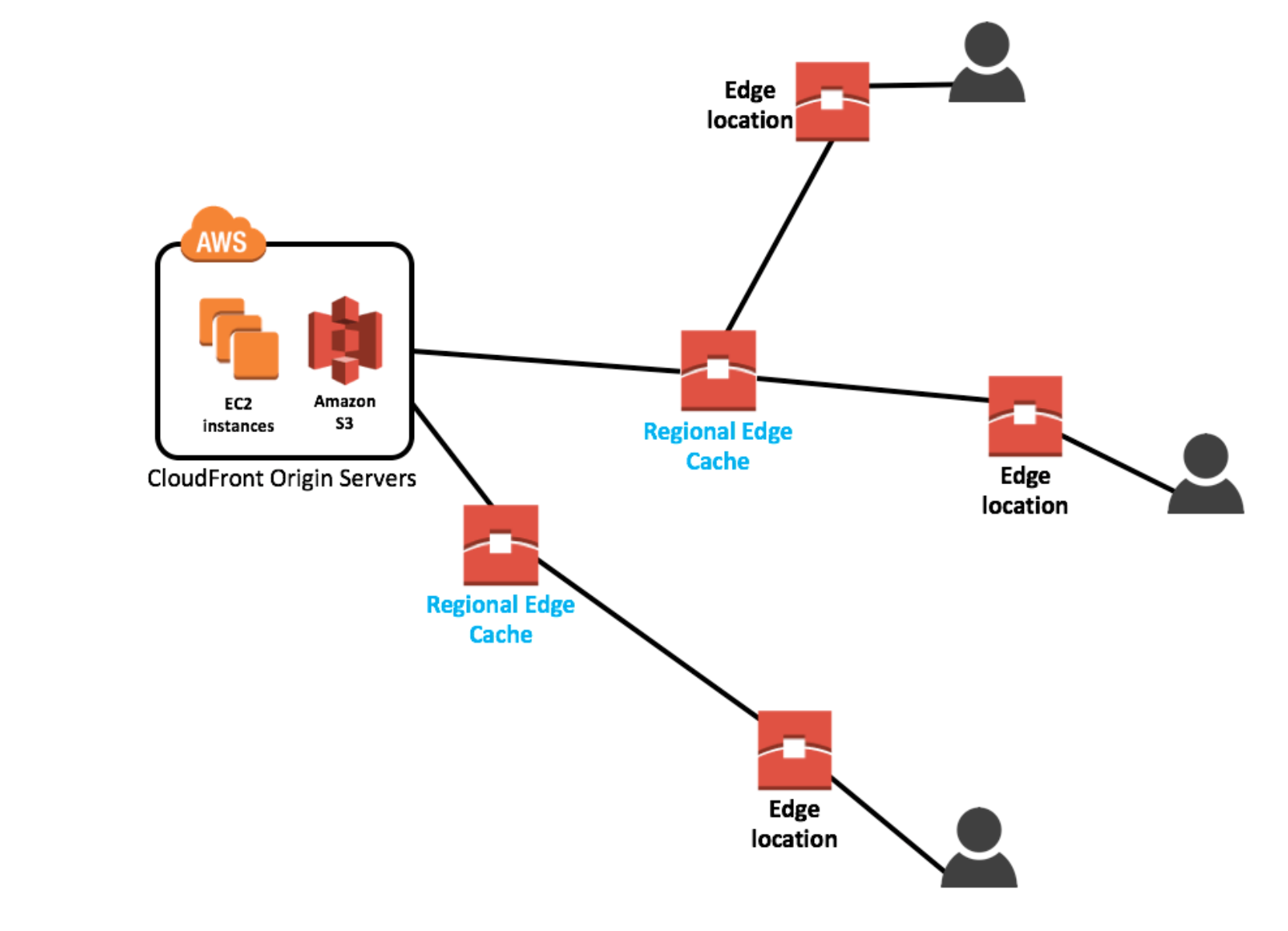
In November 2016, AWS announced a new type of Edge Location, called a Regional Edge Cache. These sit between your CloudFront Origin servers and the Edge Locations.
A Regional Edge Cache has a larger cache-width than each of the individual Edge Locations, and because data expires from the cache at the Edge Locations, the data is retained at the Regional Edge Caches.Therefore, when data is requested at the Edge Location that is no longer available, the Edge Location can retrieve the cached data from the Regional Edge Cache instead of the Origin servers, which would have a higher latency
Local Zones 🌐¶
In 2022, Amazon announced that it had launched its first 16 Local Zones, a new type of infrastructure deployment designed to place core AWS Compute, Storage, Networking, and Database services near highly populated areas such as major cities that do not already have an AWS Region nearby.
Example
Eastern United States has two Regions: us-east-1 in northern Virginia and us-east-2 in Ohio. However, there are also very large metropolitan areas around Boston, New York City, Philadelphia, Atlanta, and Miami, all of which are 100 miles or more from the data centers in that Region’s nearest Availability Zones
AWS Local Zones allow customers in these areas to deploy resources and applications that require single-digit millisecond latency that would otherwise not be attainable given the geographic distance to the nearest Regions. They are also useful where data residency requirements may dictate that data be stored within certain geographic boundaries.
Outposts 📬¶
AWS Outposts brings the capabilities of the AWS cloud to your on-premises data center. This includes the same hardware used by AWS within their data centers, allowing you to use native AWS services, including the same tools and APIs you would use when running your infrastructure within AWS.
Outposts are available as 1U or 2U rack-mountable servers, or as entire 42U racks that can be scaled to deployments of up to 96 racks. Outposts may be connected to AWS using either a Direct Connect or VPN connection. Outposts allow you to run AWS services such as EC2, ECS, EKS, S3, RDS, and EMR on-premises. Customers can also make use of PrivateLink gateway endpoints to securely and privately connect to other services and resources, such as DynamoDB. There are a wide number of EC2 instance types available on AWS Outposts.
These include M5, C5, and R5 instances, as well as storage options for EBS volumes, local disks, and localinstance storage.
Because AWS Outposts are fully managed, you do not need to maintain a level of patch management across your infrastructure or worry about installing or updating any software. AWS will ensure your Outposts are patched and updated as needed.
Bastion Host 🔒¶
A bastion host is a special-purpose computer on a network specifically designed and configured to withstand attacks. The computer generally hosts a single application, for example, a proxy server, and all other services are removed or limited to reduce the threat to the computer. It is hardened
In AWS, a bastion host is a server whose purpose is to provide access to a private network from an external network, such as the Internet. Because of its exposure to potential attacks, a bastion host must minimize the chances of penetration.
For users to talk to a private instance, we place a bastion host in a public subnet that is connected to the instance in a private subnet
Pre Signed URL 🔗¶
Info
A user who does not have AWS credentials or permission to access an S3 object can be granted temporary access by using a pre-signed URL
A pre-signed URL is generated by an AWS user who has access to the object. The generated URL is then given to the unauthorized user. The pre-signed URL can be entered in a browser or used by a program or HTML webpage. The credentials used by the pre-signed URL are those of the AWS user who generated the URL
Dedicated instances 💾¶
Instances run on hardware that is dedicated to a host.
Dedicated Host 🏢¶
In this case, the whole server is dedicated to a particular host. It is used in case, where a company has a security policy.
VPC peering ♾️¶
TLDR
A VPC peering connection is a networking connection between two VPCs that enables you to route traffic between them using private IPv4 addresses or IPv6 addresses. Instances in either VPC can communicate with each other as if they are within the same network.
You can create a VPC peering connection between your own VPCs, or with a VPC in another AWS account. The VPCs can be in different regions (also known as an inter-region VPC peering connection). This allows VPC resources including EC2 instances, Amazon RDS databases, and Lambda functions that run in different AWS Regions to communicate with each other using private IP addresses, without requiring gateways, VPN connections, or separate network appliances. The traffic remains in the private IP space. All inter-region traffic is encrypted with no single point of failure, or bandwidth bottleneck.
A VPC peering connection is a one to one relationship between two VPCs. You can create multiple VPC peering connections for each VPC that you own, but transitive peering relationships are not supported.
NAT Gateway 🌉¶
- NAT gateway is a managed NAT service.
- We create
NAT instancein a public subnet so that it can talk to the internet.
Lift and shift 🏋️♀️¶
Lift and shiftis a strategy for migrating a workload to the cloud without redesigning the application or making code changes.- It is also called as
rehosting.
APN 🛜¶
The AWS Partner Network (APN) is a global community that leverages AWS technologies, programs, expertise, and tools to build solutions and services for customers. The APN has more than 130,000 partners from over 200 countries, with 70% headquartered outside of the United States (As of October 2023)
-
CSP: Cloud Service Provider like AWS, Azure
-
MSP: Managed Service Provider like CloudReach or CloudOps
The AWS Cloud Adoption Framework (AWS CAF) identifies common cloud migration activities and best practices to optimize your migrations and cloud adoption outcomes.
The AWS Cloud Adoption Readiness Tool (CART) helps customers develop efficient and effective plans for cloud adoption and enterprise cloud migrations