VPC ¶
A networking service that you can use to establish boundaries around your AWS resources is Amazon Virtual Private Cloud (VPC)
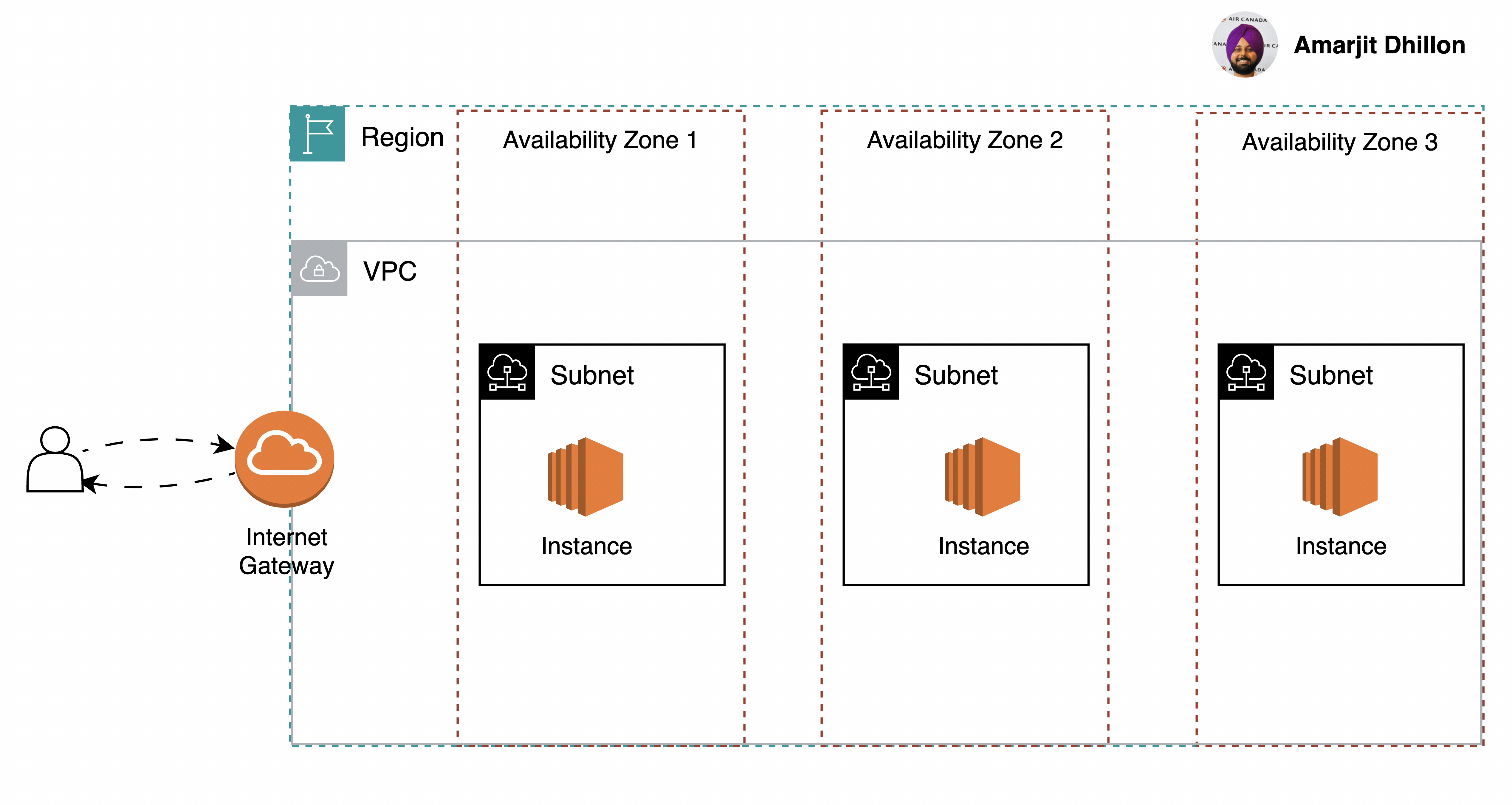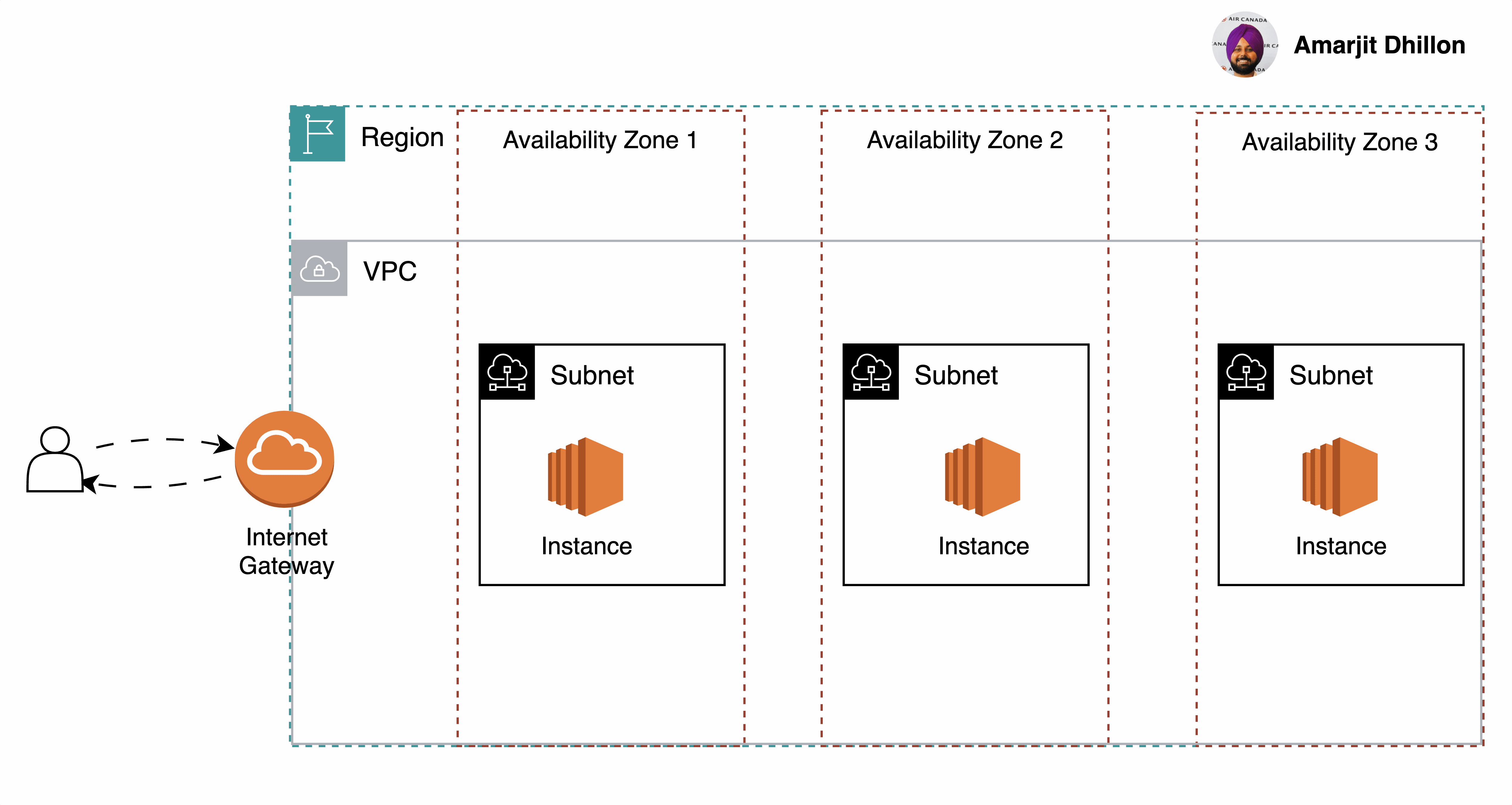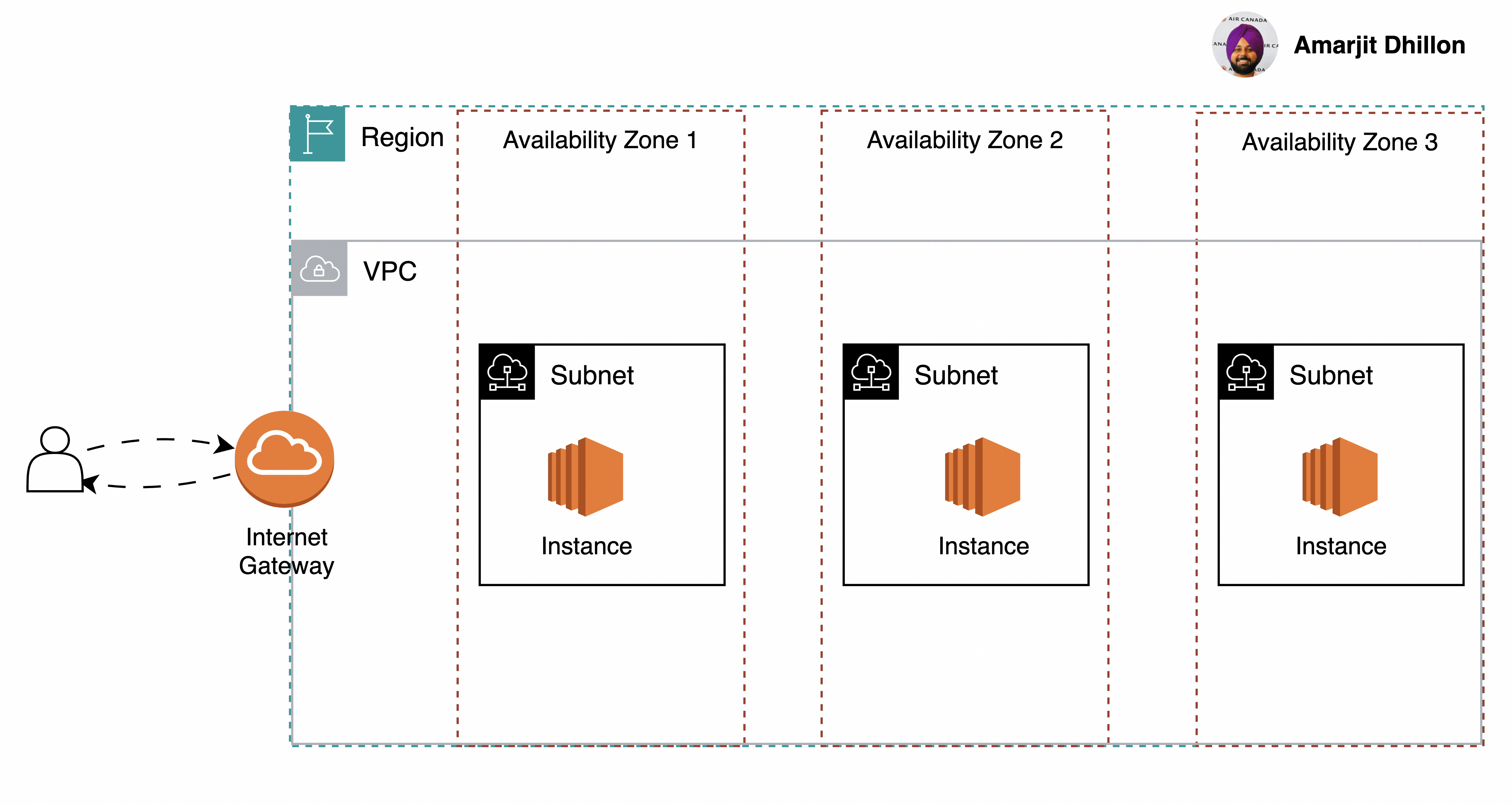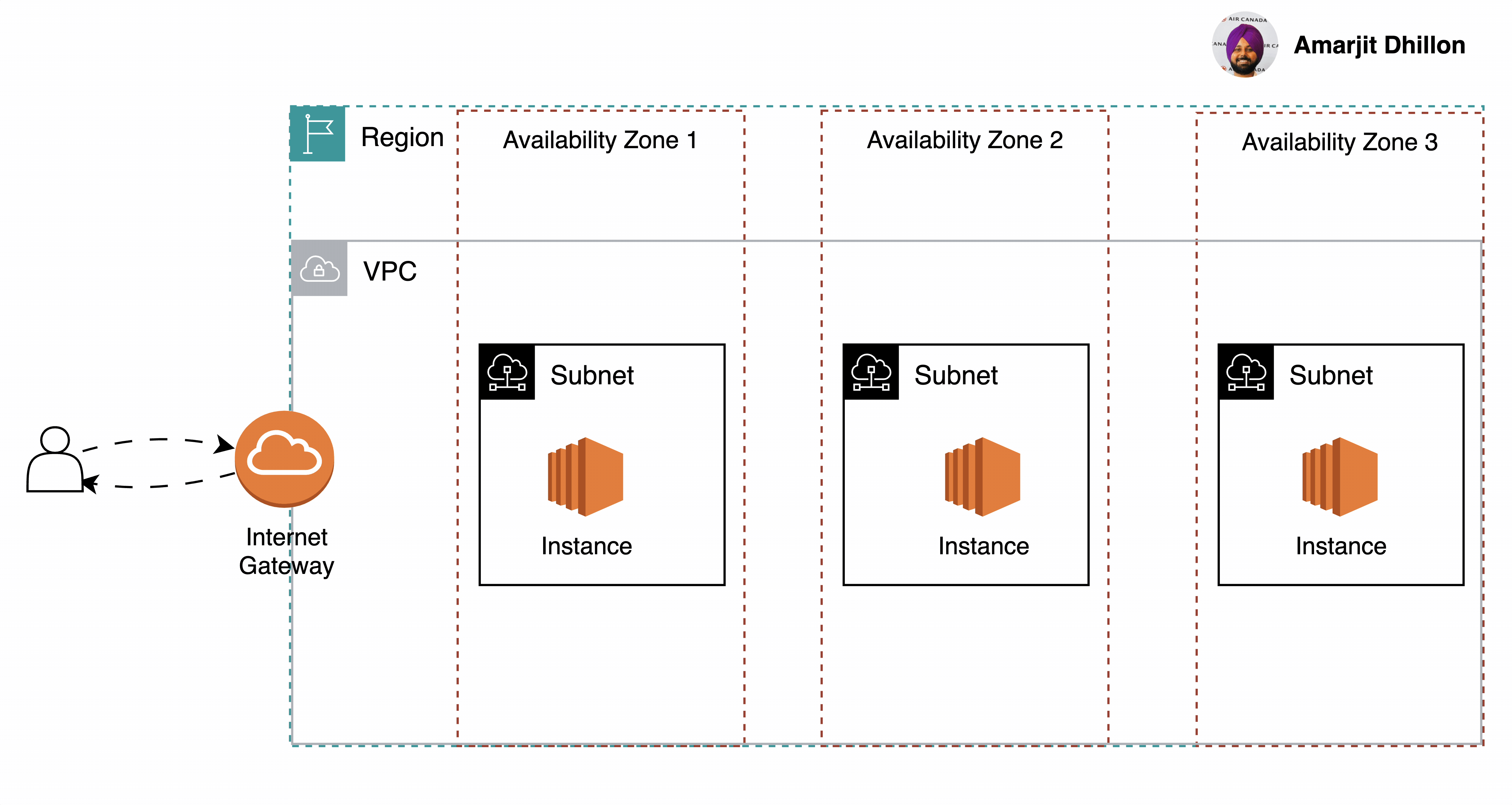
Virtual Private Gateway is shown below
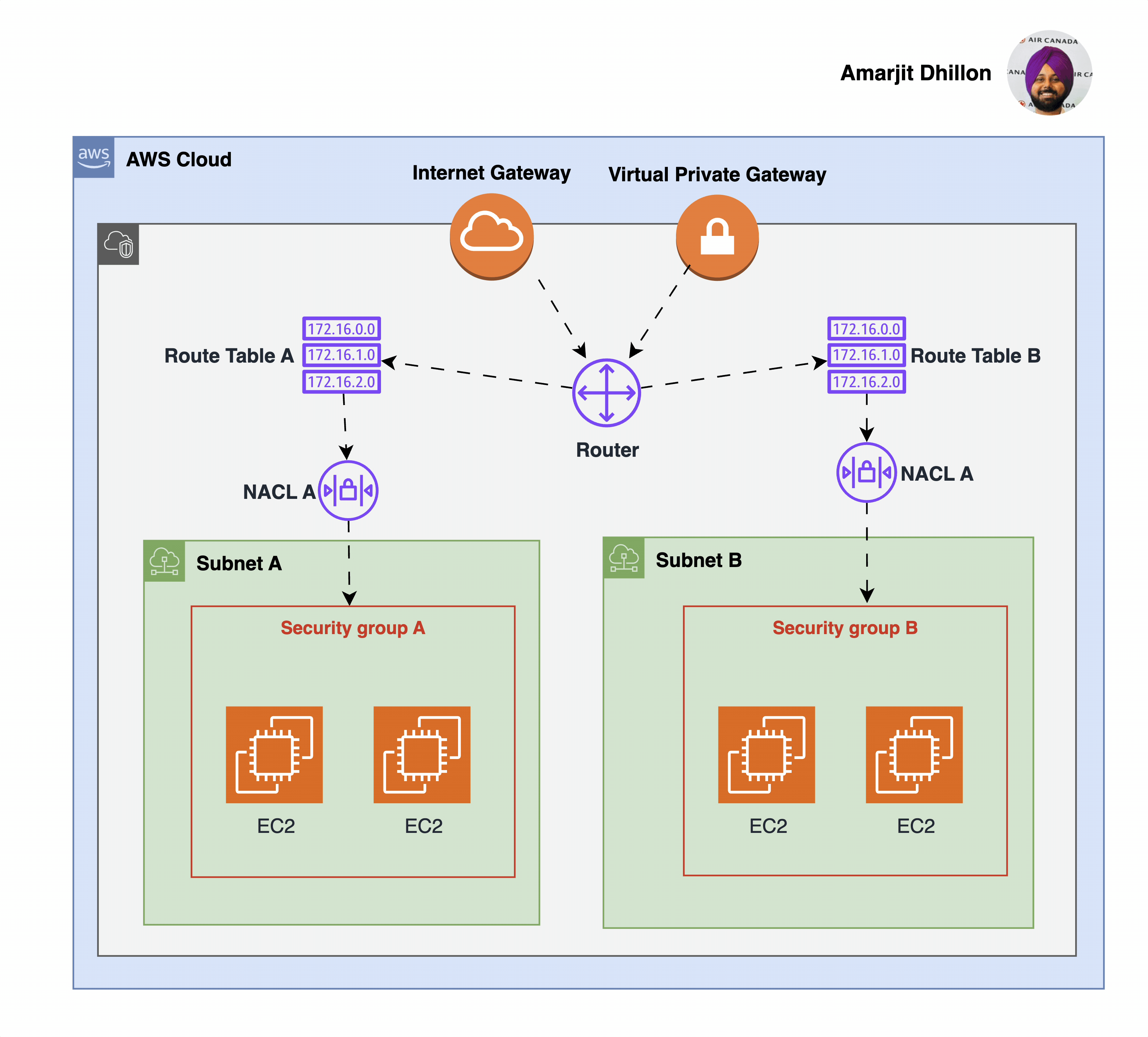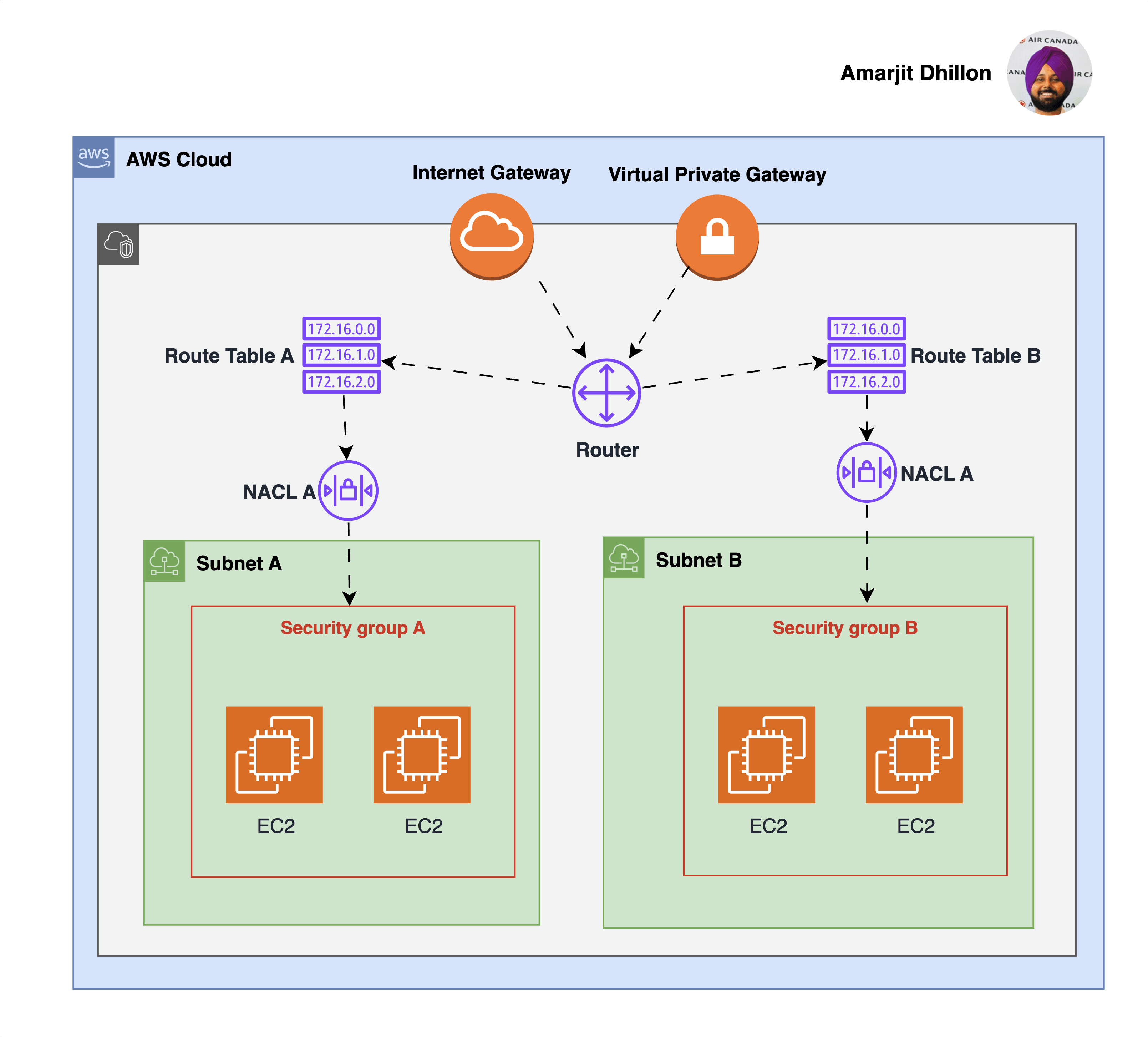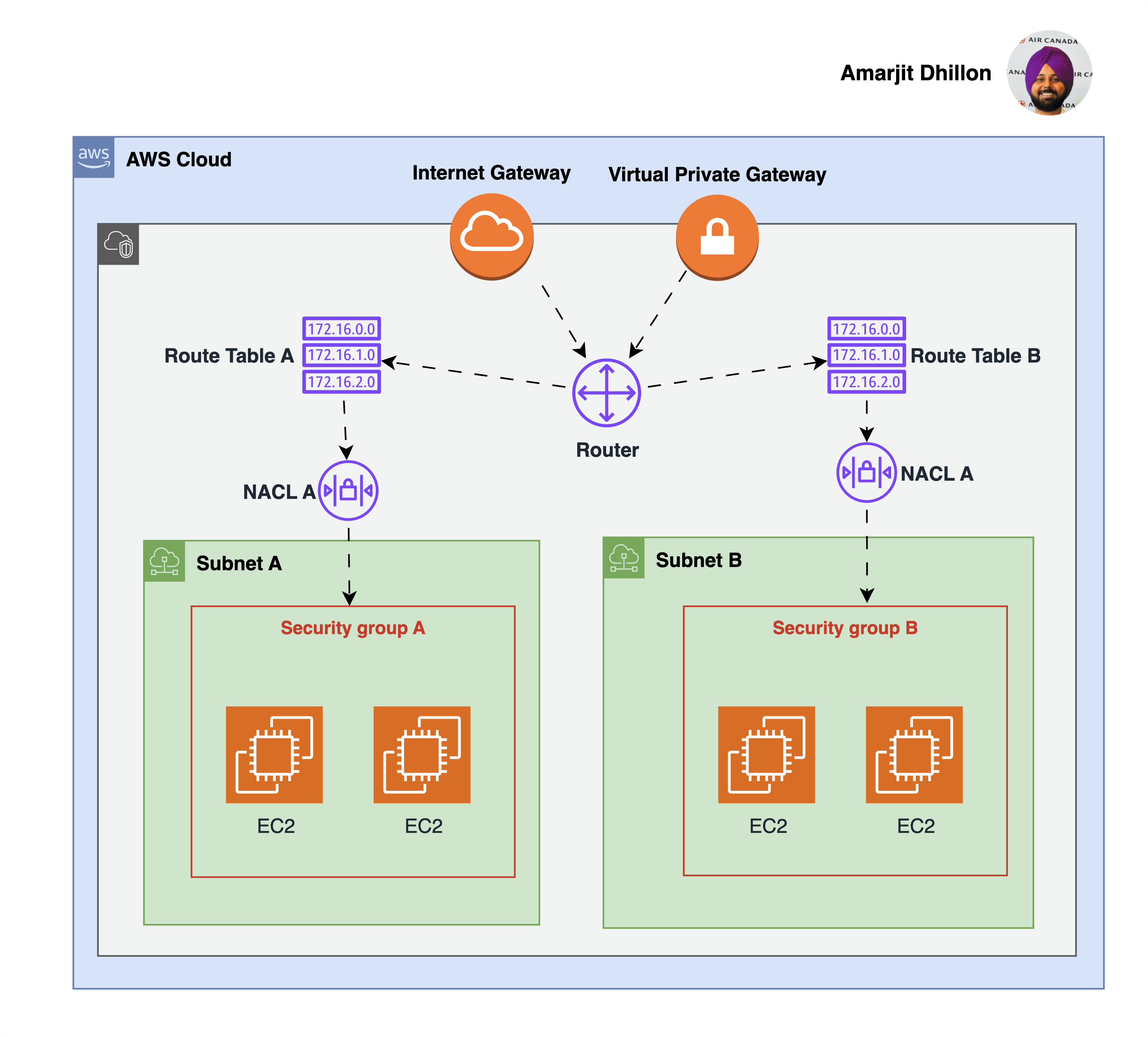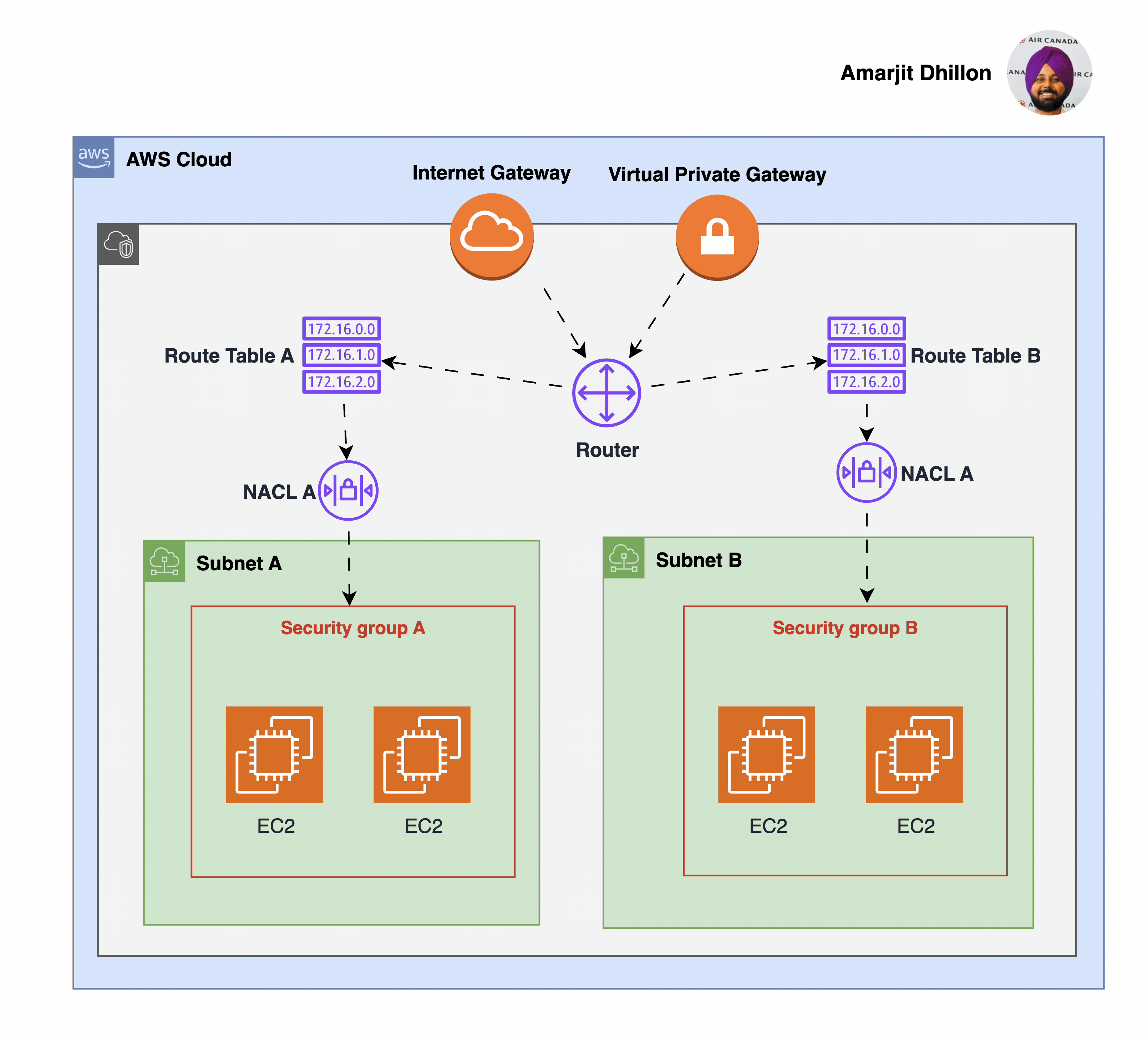
The Virtual Private Gateway (VPG) is the component that allows protected internet traffic to enter into the VPC.
Key Takeaway
A virtual private gateway enables you to establish a virtual private network (VPN) connection between your VPC and a private network, such as an on-premises data center or internal corporate network.
A virtual private gateway allows traffic into the VPC only if it is coming from an approved network.
Here is an exmaple of 3 tier web applicaiton
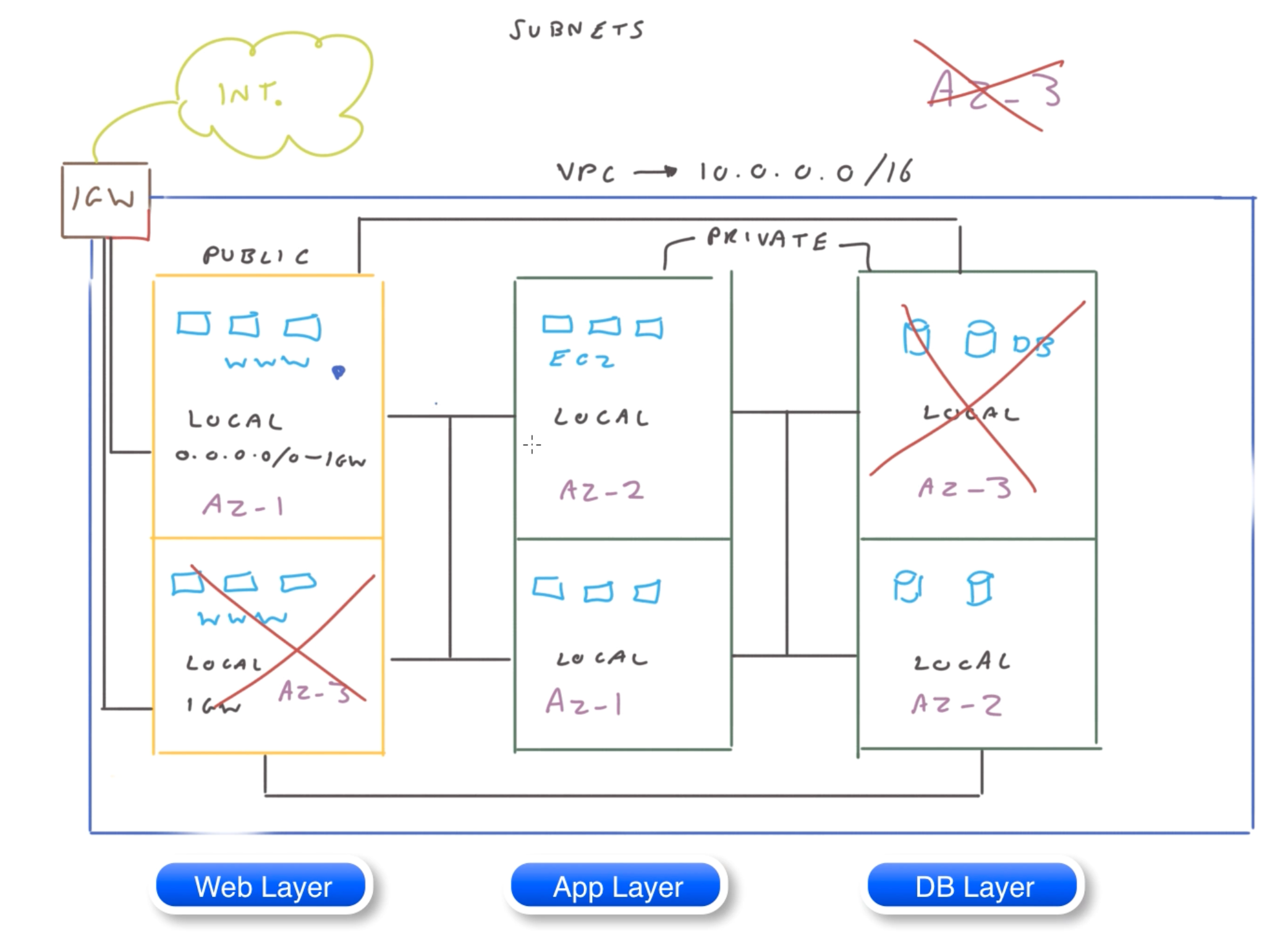
Elements in VPC 🌐¶
Elastic Network Interface 🔗¶
It is a logical networking component in a VPC that represents a virtual network card.
Subnet 🥅¶
- A range of IP addresses in your VPC. You can add AWS resources to a specified subnet.
- Use a
public subnetfor resources that must connect to the internet, and aprivate subnetfor resources that don't connect to the internet.
Security group 🚔¶
A security group controls the traffic that is allowed to reach and leave the resources that it is associated with. For example, after you associate a security group with an EC2 instance, it controls the inbound and outbound traffic for the instance.
SG are stateful
Security groups are stateful.
For example, if you send a request from an instance, the response traffic for that request is allowed to reach the instance regardless of the inbound security group rules. Responses to allowed inbound traffic are allowed to leave the instance, regardless of the outbound rules.
Security Group Rules
-
You can specify allow rules, but not deny rules ❌
-
When you first create a security group, it has no inbound rules. Therefore, no inbound traffic is allowed until you add inbound rules to the security group.
-
When you first create a security group, it has an outbound rule that allows all outbound traffic from the resource. You can remove the rule and add outbound rules that allow specific outbound traffic only. If your security group has no outbound rules, no outbound traffic is allowed.
-
When you associate multiple security groups with a resource, the rules from each security group are aggregated to form a single set of rules that are used to determine whether to allow access.
-
When you add, update, or remove rules, your changes are automatically applied to all resources associated with the security group.
-
The effect of some rule changes can depend on how the traffic is tracked.
-
When you create a security group rule, AWS assigns a
unique IDto the rule. You can use the ID of a rule when you use the API or CLI to modify or delete the rule
When you create a VPC, it comes with a default security group. You can create additional security groups for a VPC, each with their own inbound and outbound rules. You can specify the source, port range, and protocol for each inbound rule. You can specify the destination, port range, and protocol for each outbound rule.
Security Group naming rules
-
You can assign a security group only to resources created in the same VPC as the security group. You can assign multiple security groups to a resource.
-
When you create a security group, you must provide it with a name and a description. The following rules apply:
- A security group name must be unique within the VPC.
- Names and descriptions can be up to 255 characters in length.
- Names and descriptions are limited to the following characters: a-z, A-Z, 0-9, spaces, and ._-:/()#,@[]+=&;{}!$*.
- When the name contains trailing spaces, we trim the space at the end of the name. For example, if you enter "Test Security Group " for the name, we store it as "Test Security Group".
- A security group name cannot start with sg-.
- Security groups are stateful. For example, if you send a request from an instance, the response traffic for that request is allowed to reach the instance regardless of the inbound security group rules. Responses to allowed inbound traffic are allowed to leave the instance, regardless of the outbound rules.
NACL 📋¶
A network access control list (ACL) allows or denies specific inbound or outbound traffic at the subnet level.
You can use the default network ACL for your VPC, or you can create a custom network ACL for your VPC with rules that are similar to the rules for your security groups in order to add an additional layer of security to your VPC.
Example
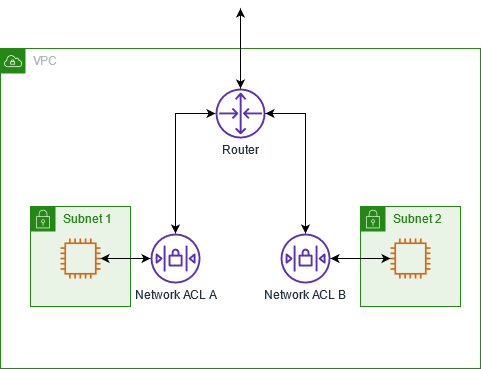
The following diagram shows a VPC with two subnets. Each subnet has a network ACL. When traffic enters the VPC (for example, from a peered VPC, VPN connection, or the internet), the router sends the traffic to its destination.
Network ACL A determines which traffic destined for subnet 1 is allowed to enter subnet 1, and which traffic destined for a location outside subnet 1 is allowed to leave subnet 1.
Similarly, network ACL B determines which traffic is allowed to enter and leave subnet 2
-
A subnet can only be associated with a single NACL at a time.
-
The default subnet ACL allows all inbound and outbound traffic.
-
NACL rules have
- Rule number
- Protocol
- Choice of ALLOW or DENY
CIDR rangePorstorport rangefor inbound and outbound traffic
Few notes about NACL
The following are the basic things that you need to know about network ACLs:
-
Your VPC automatically comes with a modifiable default network ACL. By default, it allows all inbound and outbound IPv4 traffic and, if applicable, IPv6 traffic.
-
You can create a
custom network ACLand associate it with a subnet to allow or deny specific inbound or outbound traffic at the subnet level. -
Each subnet in your VPC must be associated with a network ACL. If you don't explicitly associate a subnet with a network ACL, the subnet is automatically associated with the default network ACL.
-
You can associate a network ACL with multiple subnets. However, a subnet can be associated with only one network ACL at a time. When you associate a network ACL with a subnet, the previous association is removed.
-
A network ACL has inbound rules and outbound rules. Each rule can either allow or deny traffic. Each rule has a number from 1 to 32766. We evaluate the rules in order, starting with the lowest numbered rule, when deciding whether allow or deny traffic. If the traffic matches a rule, the rule is applied and we do not evaluate any additional rules. We recommend that you start by creating rules in increments (for example, increments of 10 or 100) so that you can insert new rules later on, if needed.
-
We evaluate the network ACL rules when traffic enters and leaves the subnet, not as it is routed within a subnet.
-
NACLs are
stateless, which means that information about previously sent or received traffic is not saved. If, for example, you create a NACL rule to allow specific inbound traffic to a subnet, responses to that traffic are not automatically allowed. This is in contrast to how security groups work. Security groups are stateful, which means that information about previously sent or received traffic is saved. If, for example, a security group allows inbound traffic to an EC2 instance, responses are automatically allowed regardless of outbound security group rules.
Route table 📑¶
-
It contains a set of routes that AWS uses to direct the network traffic for your VPC.
-
You can explicitly associate a subnet with a particular route table.
Main route table and subnet association
By default, the subnet is associated with the main route table
Route 🛣️¶
Each route in a route table specifies a range of IP addresses and the destination where Lambda sends the traffic for that range. The route also specifies a target, which is the gateway, network interface, or connection through which to send the traffic.
NAT gateway 🌉¶
An AWS Network Address Translation (NAT) service that controls access from a private VPC private subnet to the Internet.
VPC endpoints 🖇️¶
You can use an Amazon VPC endpoint to create private connectivity to services hosted in AWS, without requiring access over the internet or through a NAT device, VPN connection, or AWS Direct Connect connection.
VPC flow logs 📕¶
VPC Flow Logs is a feature that enables you to capture information about the IP traffic going to and from network interfaces in your VPC.
We can use them for troubleshooting to see if there is some attack on the VPC. Also, they can let us know why the communication between the VPC’s is not working out.
You can create a flow log for a VPC, a subnet, or a network interface. If you create a flow log for a subnet or VPC, each network interface in that subnet or VPC is monitored.
VPC Peering 🪙¶
A VPC peering connection is a networking connection between two VPCs that enables you to route traffic between them using private IPv4 addresses or IPv6 addresses.
Instances in either VPC can communicate with each other as if they are within the same network. You can create a VPC peering connection between your own VPCs, or with a VPC in another AWS account.
The VPCs can be in different Regions (also known as an inter-Region VPC peering connection).
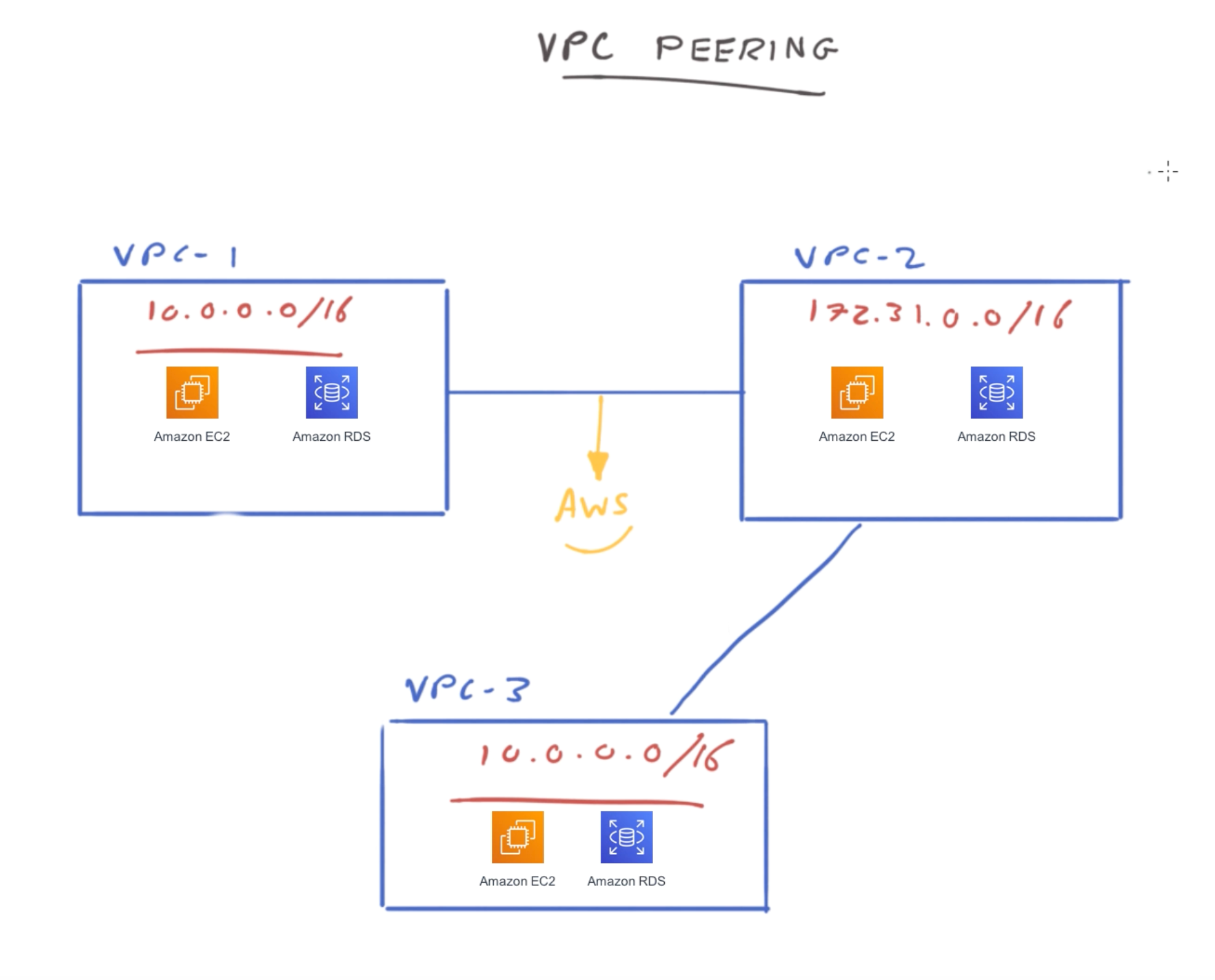
No IP Overlap
AWS uses the existing infrastructure of a VPC to create a VPC peering connection; it is neither a gateway nor a VPN connection, and does not rely on a separate piece of physical hardware. There is no single point of failure for communication or a bandwidth bottleneck.
VPC Sharing 🔍¶
Why is VPC sharing requried?
Sharing VPCs is useful when network isolation between teams does not need to be strictly managed by the VPC owner, but the account level users and permissions must be.
With Shared VPC, multiple AWS accounts create their application resources (such as Amazon EC2 instances) in shared, centrally managed Amazon VPCs.
In this model, the account that owns the VPC (owner) shares one or more subnets with other accounts (participants). After a subnet is shared, the participants can view, create, modify, and delete their application resources in the subnets shared with them.
Participants cannot view, modify, or delete resources that belong to other participants or the VPC owner. Security between resources in shared VPCs is managed using security groups, network access control lists (NACLs), or through a firewall between the subnets.
VPC sharing allows multiple AWS accounts to create their application resources, such as Amazon EC2 instances, Amazon Relational Database Service (RDS) databases, Amazon Redshift clusters, and AWS Lambda functions, into shared, centrally-managed virtual private clouds (VPCs).
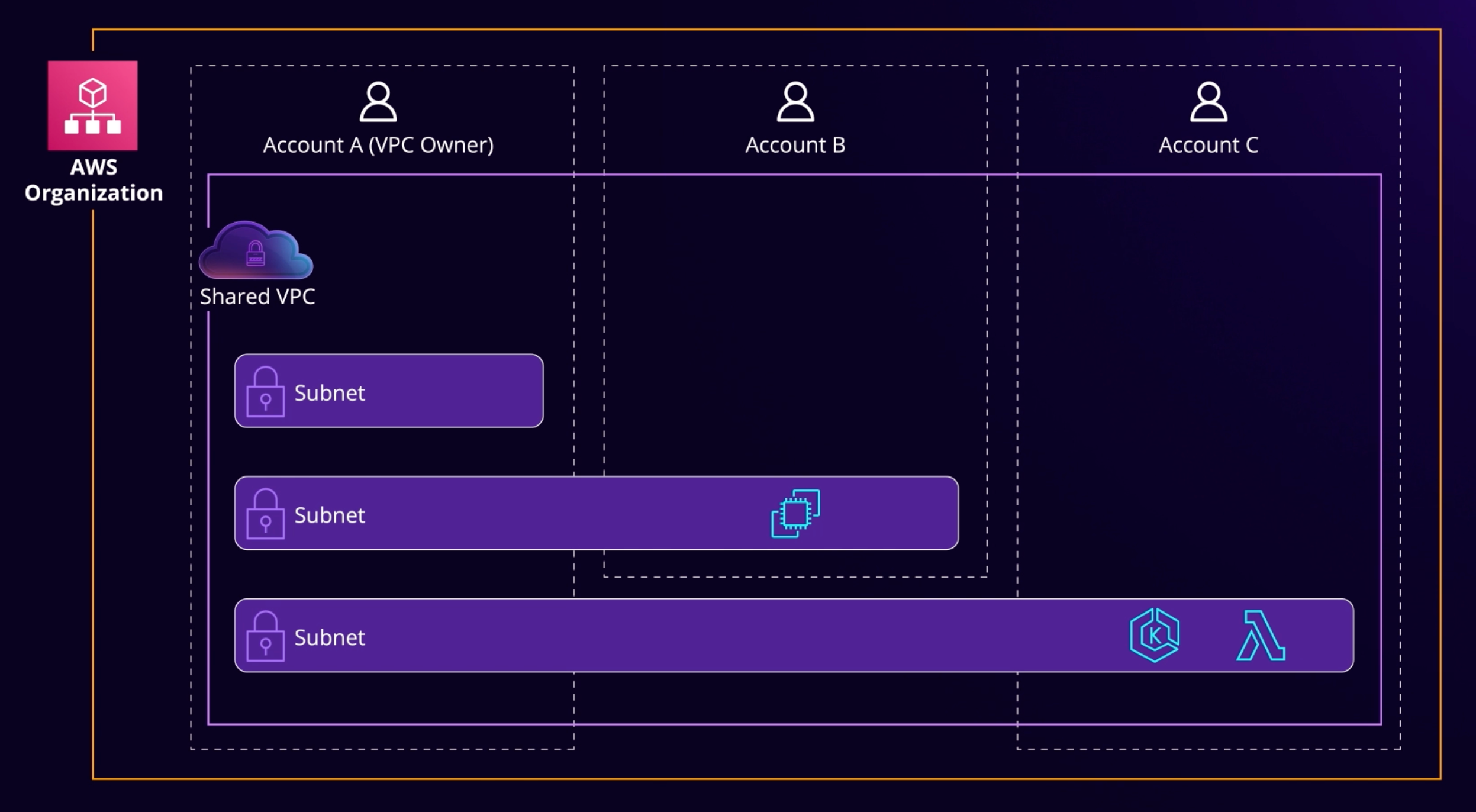
In this model, the account that owns the VPC (owner) shares one or more subnets with other accounts (participants) that belong to the same organization from AWS Organizations.
After a subnet is shared, the participants can view, create, modify, and delete their application resources in the subnets shared with them. Participants cannot view, modify, or delete resources that belong to other participants or the VPC owner.
VPC Endpoints ⚡️¶
A VPC endpoint enables customers to privately connect to supported AWS services and VPC endpoint services powered by AWS PrivateLink. Amazon VPC instances do not require public IP addresses to communicate with resources of the service. Traffic between an Amazon VPC and a service does not leave the Amazon network.
VPC endpoints are virtual devices. They are horizontally scaled, redundant, and highly available Amazon VPC components that allow communication between instances in an Amazon VPC and services without imposing availability risks or bandwidth constraints on network traffic. There are two types of VPC endpoints:
-
Interface endpoints: Interface endpoints enable connectivity to services over AWS PrivateLink. These services include some
AWS managed services, services hosted by otherAWS customersand partners in their own Amazon VPCs (referred to as endpoint services), and supported AWS Marketplace partner services. The owner of a service is a service provider. The principal creating the interface endpoint and using that service is a service consumer. -
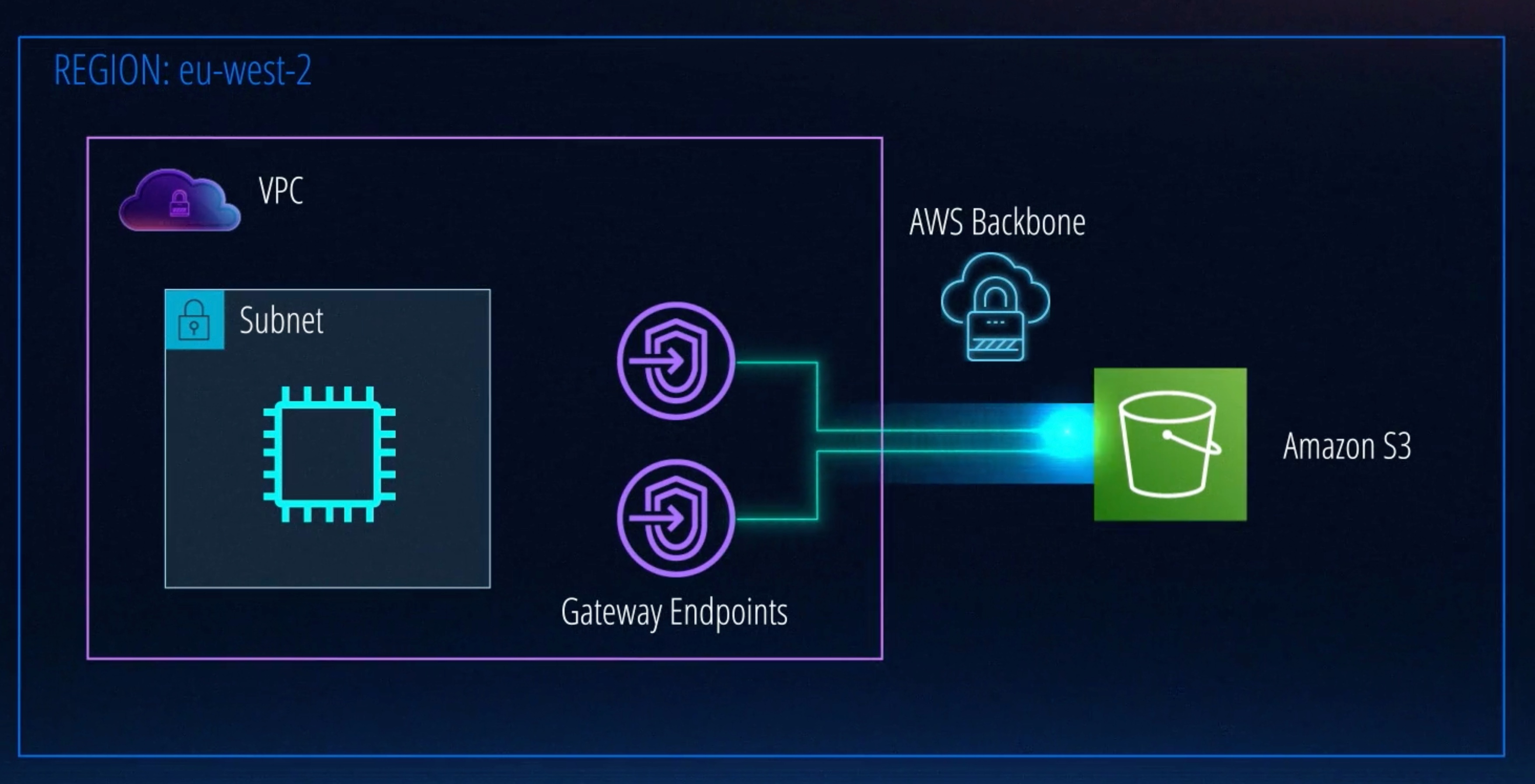
Gateway endpoints: A gateway endpoint targets specific IP routes in an Amazon VPC route table, in the form of a prefix-list, used for traffic destined to
Amazon DynamoDBorAmazon S3. Gateway endpoints do not enable AWS PrivateLink.
Remember
Interface Endpoints use PrivateLink to establish a private and secure connection, while Gateway Endpoints are used within route tables to reach supported services.
Dynamic Routing 🚏¶
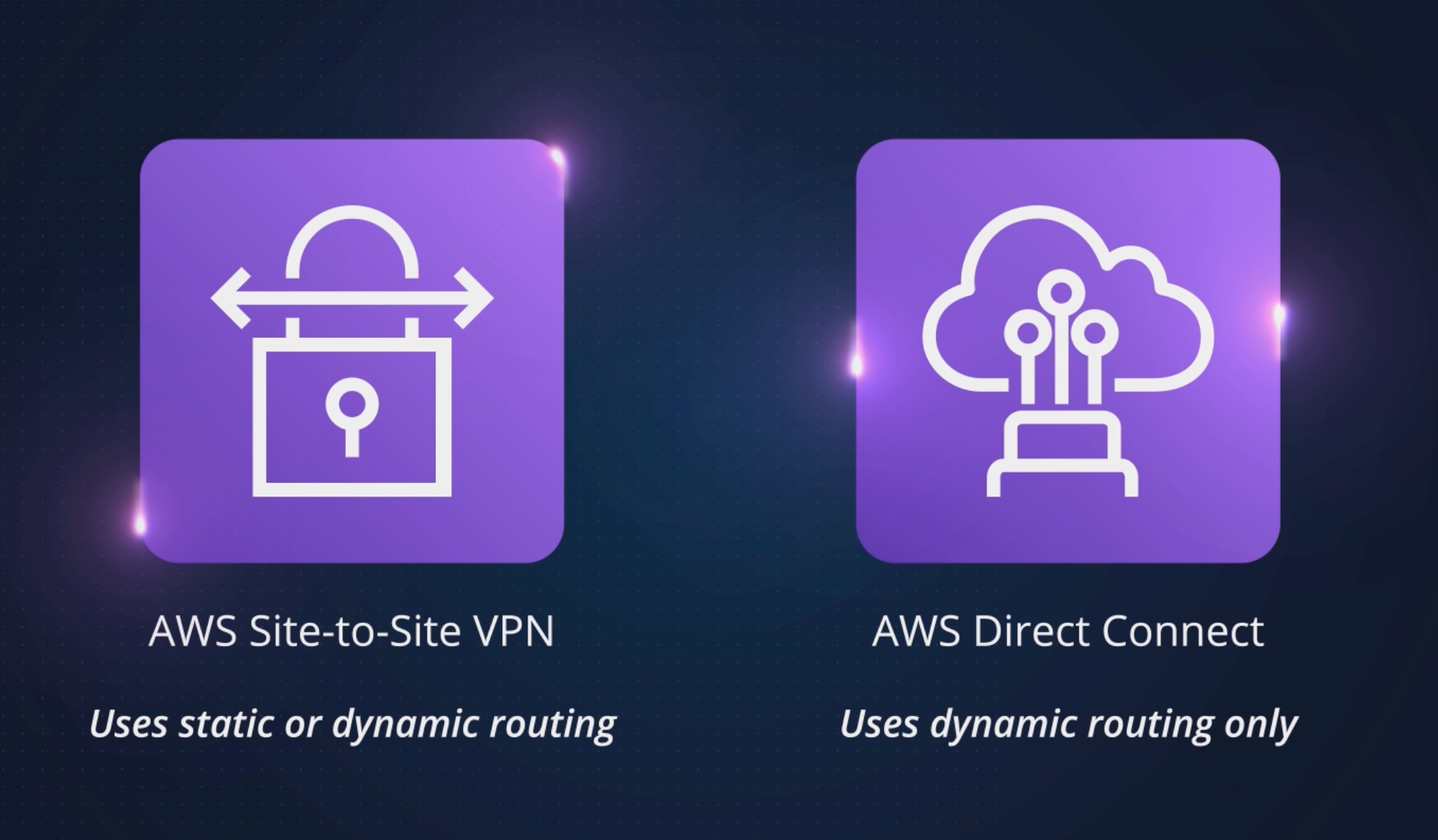
The type of routing that you select can depend on the make and model of your customer gateway device. If your customer gateway device supports Border Gateway Protocol (BGP), specify dynamic routing when you configure your Site-to-Site VPN connection.
If your customer gateway device does NOT support BGP, specify static routing.
Customer Managed S2S VPN 🌐¶
One advantage of customer-managed site-to-site VPNs is that you can control the protocols that your connection uses for authentication, integrity checks, and encryption. When using VPC peering, you have no control of security protocols use to secure traffic.
Notes¶
Some notes on VPC are
-
NACL applies to all instances in an associated subnet.
-
NACLs are always evaluated first because they exist at the border of a subnet. As
security groupsare attached to instances, they are not processed until traffic passes through the NACL and into the instance’s subnet. -
NACLs are associated with subnets, not VPC.
-
Each rule in an NACL has a number, and those rules are evaluated using those numbers, moving from low to high.
-
Each subnet in your VPC must be associated with an NACL.
-
An NACL is associated with a subnet, not an instance or VPC. It can be associated with a single subnet or multiple subnets.
-
A VPC spans all the availability zones in a region.
-
You must always select a region to create a VPC, and you must always provide a CIDR block. VPCs span all the AZs in a region, so that is not required.
-
While you can add secondary IPv4 CIDR blocks, you cannot add additional CIDR blocks for IPv6 at this time.
-
When creating a VPC, you can specify an option name (no description needed), a required IPv4 CIDR block, and an optional IPv6 CIDR block.
-
A VPN-only subnet routes traffic through a virtual private gateway rather than an internet gateway
-
At a minimum, a VPC-only subnet must have a routing table routing traffic and a virtual private gateway to which traffic is routed.
-
You can only create 5 VPCs per region by default. Creating more requires a request to AWS.
-
You can create 200 subnets per VPC.
-
You’re allowed 5 elastic IP addresses per region unless you have the default limits raised by AWS.
-
A security group denies all traffic unless explicitly allowed. This means it functions as a whitelist.
-
A VPC endpoint is a connection to an AWS service and explicitly does not use internet gateways or VPN connections.
-
Internet gateways scale horizontally, not vertically. They are also redundant and highly available automatically.
-
Default VPC has an internet gateway automatically attached.
-
Load Balancers
-
Application load balancersoperate at the Application layer, which is layer 7 of the OSI model. -
ELBs(classic load balancers) operate at the Transport layer, layer 4, as well as layer 7. -
Network load balancersoperate at layer 4 as well
-
-
A NAT device—network address translation—provides routing for instances to an internet gateway but can prevent undesired inbound traffic.
-
A site-to-site connection is going to require a private subnet on the AWS side with private instances within it.
-
An
egress-only gatewayis for use with IPv6 traffic and only allows outbound traffic. They are stateful. -
The default VPC has an internet gateway attached by default while custom VPC do not
-
The default VPC has a CIDR block of
/16, but the default subnet in each AZ is a/20. -
Default VPC does get a subnet automatically (as well as an internet gateway).
-
While the default VPC automatically creates a subnet, while custom VPCs do not create a subnet.
-
With custom VPC, You do automatically get a security group, route table, and NACL.
-
A VPC endpoint can connect to S3 and DynamoDB, as well as a host of additional AWS services. It does not require an internet gateway or a VPN connection and does not route traffic over the public Internet.
-
A VPC endpoint is a virtual device that provides redundancy via AWS (and automatically).
-
A VPC endpoint provides a connection over the Amazon network between your VPC and service, such as S3. This avoids leaving the network and routing over the public Internet, which inherently provides greater security for the traffic involved
-
VPCs can peer with other VPCs, in the same account or different ones