Elastic Load Balancer ¶
- ELB is HA service managed by AWS
- Elastic Load Balancing automatically distributes your incoming traffic across multiple targets, such as EC2 instances, containers, and IP addresses, in one or more Availability Zones.
- It monitors the health of its registered targets, and routes traffic only to the healthy targets.
- Elastic Load Balancing scales your load balancer capacity automatically in response to changes in incoming traffic.
Load Balancer and Auto Scaling group work hand in hand
Elastic Load Balancing is the AWS service that automatically distributes incoming application traffic across multiple resources, such as Amazon EC2 instances.
A load balancer acts as a single point of contact for all incoming web traffic to your Auto Scaling group. This means that as you add or remove Amazon EC2 instances in response to the amount of incoming traffic, these requests route to the load balancer first. Then, the requests spread across multiple resources that will handle them.
Types of ELB¶
Classic LB¶
Classic load balancers support both IPv4 and IPv6. They support HTTP/1 and HTTP/1.1, but only application load balancers support HTTP/2.
Why not to use Classic LB?
You must register individual instances, rather than target groups, with classic load balancers; registering target groups is a functionality only available with application load balancers.
An ELB is an elastic load balancer and generally refers to a classic load balancer. An ALB is an application load balancer.
Classic load balancers operate at both the connection (Level 4) and the request (Level 7) layer of the TCP stack.
Application LB (L7)¶
An ALB offers SSL termination and makes the SSL offload process very simple through tight integration with SSL processes. While an ELB will handle SSL termination, it does not offer the management features that ALBs do.
Network LB (L4)¶
- A Network Load Balancer functions at the 4th layer of the Open Systems Interconnection (OSI) model.
- It can handle
millionsof requests per second. - After the
load balancerreceives a connection request, it selects atargetfrom thetarget groupfor the default rule. It attempts to open aTCP connectionto the selected target on the port specified in the listener configuration. - By default, each load balancer node distributes traffic across the registered targets in its Availability Zone only. If you enable cross-zone load balancing, each load balancer node distributes traffic across the registered targets in all enabled Availability Zones.
- For TCP traffic, the load balancer selects a target using a flow hash algorithm based on the protocol, source IP address, source port, destination IP address, destination port, and TCP sequence number. The TCP connections from a client have different source ports and sequence numbers, and can be routed to different targets. Each individual TCP connection is routed to a single target for the life of the connection.
- For UDP traffic, the load balancer selects a target using a flow hash algorithm based on the protocol, source IP address, source port, destination IP address, and destination port. A UDP flow has the same source and destination, so it is consistently routed to a single target throughout its lifetime. Different UDP flows have different source IP addresses and ports, so they can be routed to different targets.

Components of ELB¶
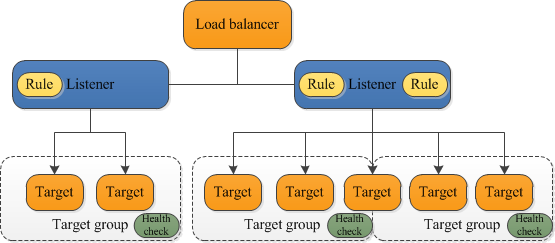
Listener¶
A listener checks for connection requests from clients, using the protocol and port that you configure.
Where is your certificate?
To create an HTTPS listener, you must deploy at least one SSL server certificate on your load balancer. The load balancer uses a server certificate to terminate the front-end connection and then decrypt requests from clients before sending them to the targets.
You must also specify a security policy, which is used to negotiate secure connections between clients and the load balancer.
Rule¶
The rules that you define for a listener determine how the load balancer routes requests to its registered targets.
Each rule consists of a priority, one or more actions, and one or more conditions. When the conditions for a rule are met, then its actions are performed. You must define a default rule for each listener, and you can optionally define additional rules.
Target/ Target Group¶
Each target group routes requests to one or more registered targets, such as EC2 instances, using the protocol and port number that you specify.
You can register a target with multiple target groups. You can configure health checks on a per target group basis. Health checks are performed on all targets registered to a target group that is specified in a listener rule for your load balancer.