AWS Org ¶
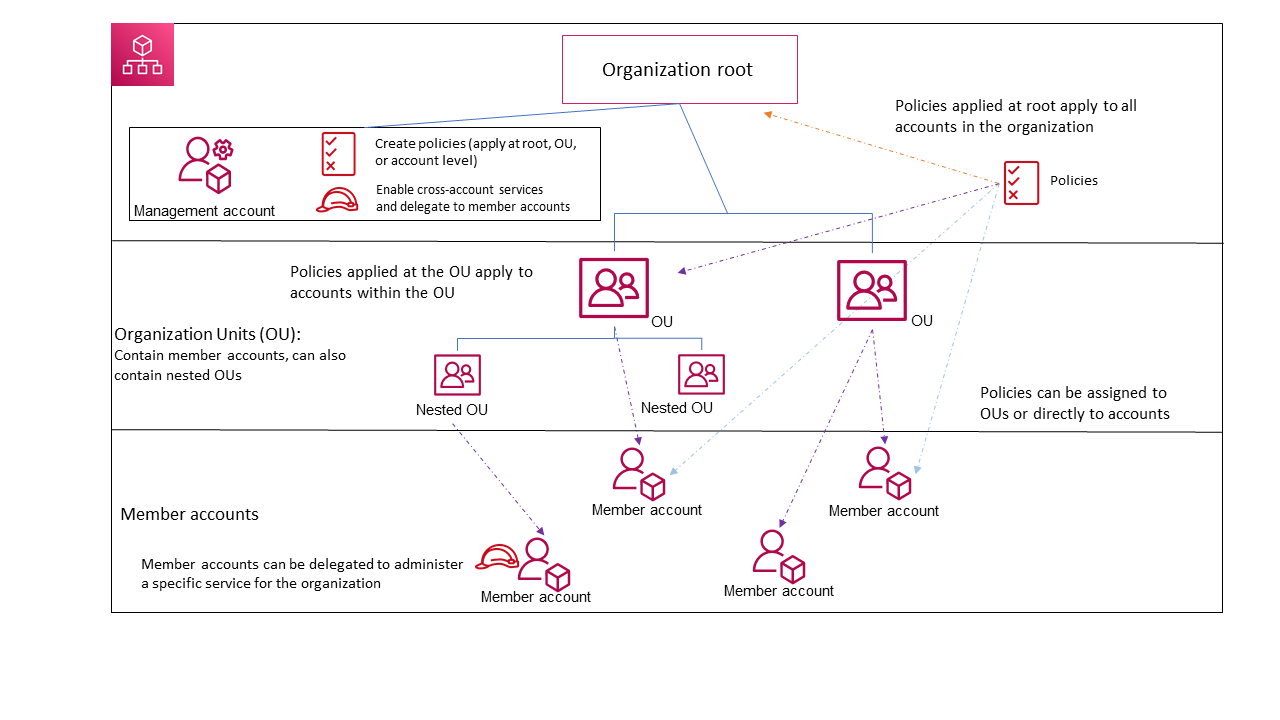
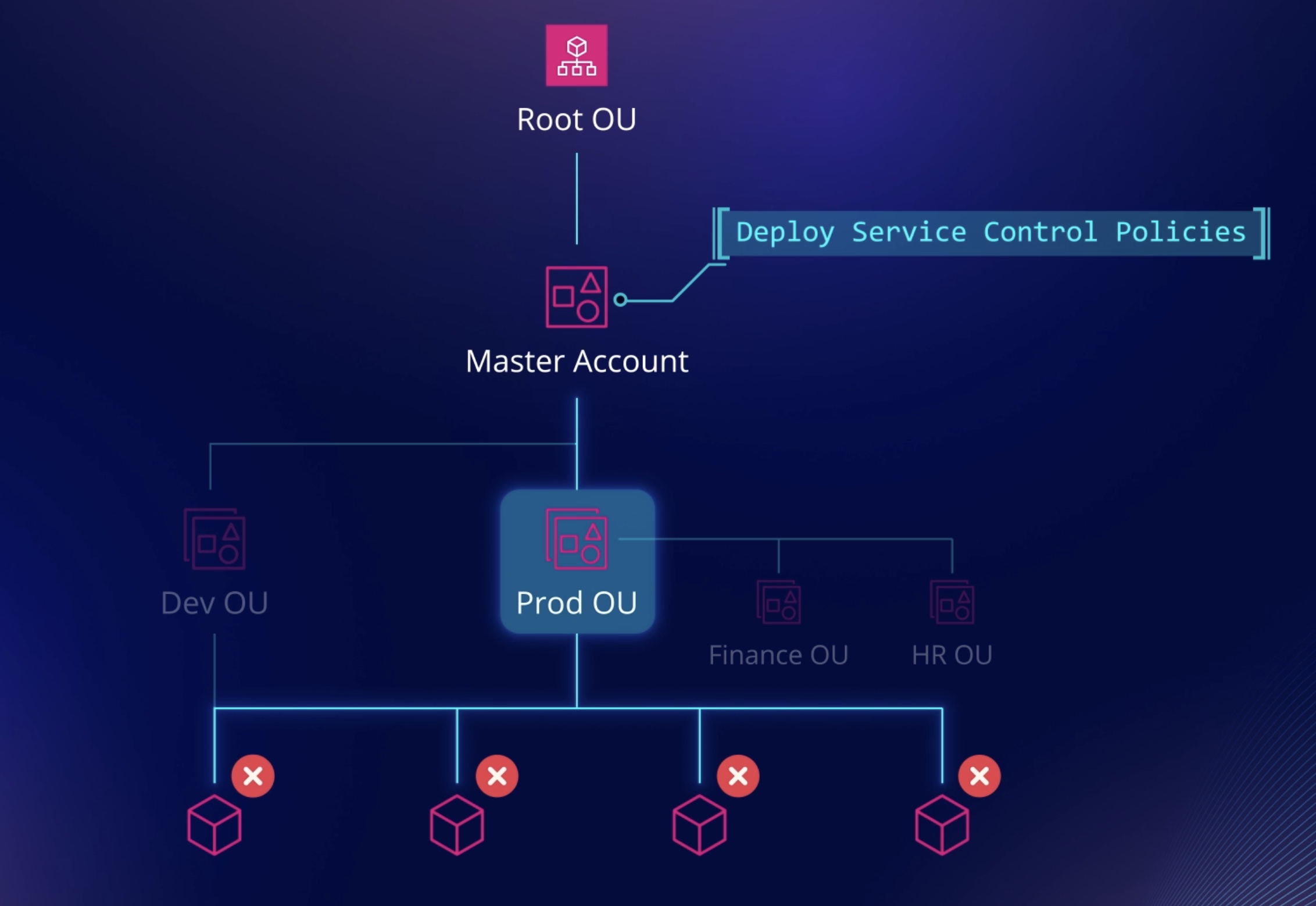
The following diagram shows a basic organization that consists of five accounts that are organized into four organizational units (OUs) under the root. The organization also has several policies that are attached to some of the OUs or directly to accounts.
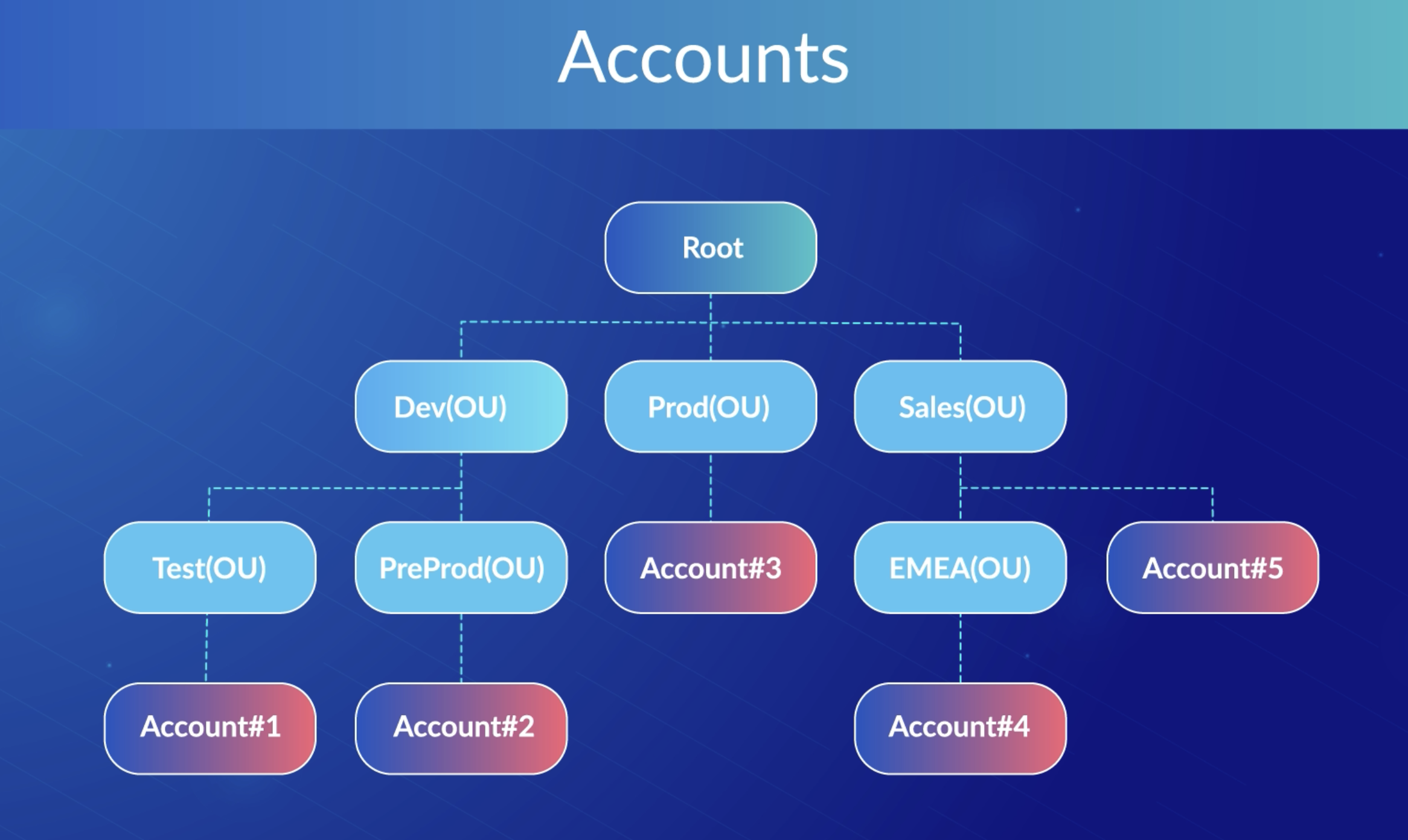
A simplified OU Tree is shown below
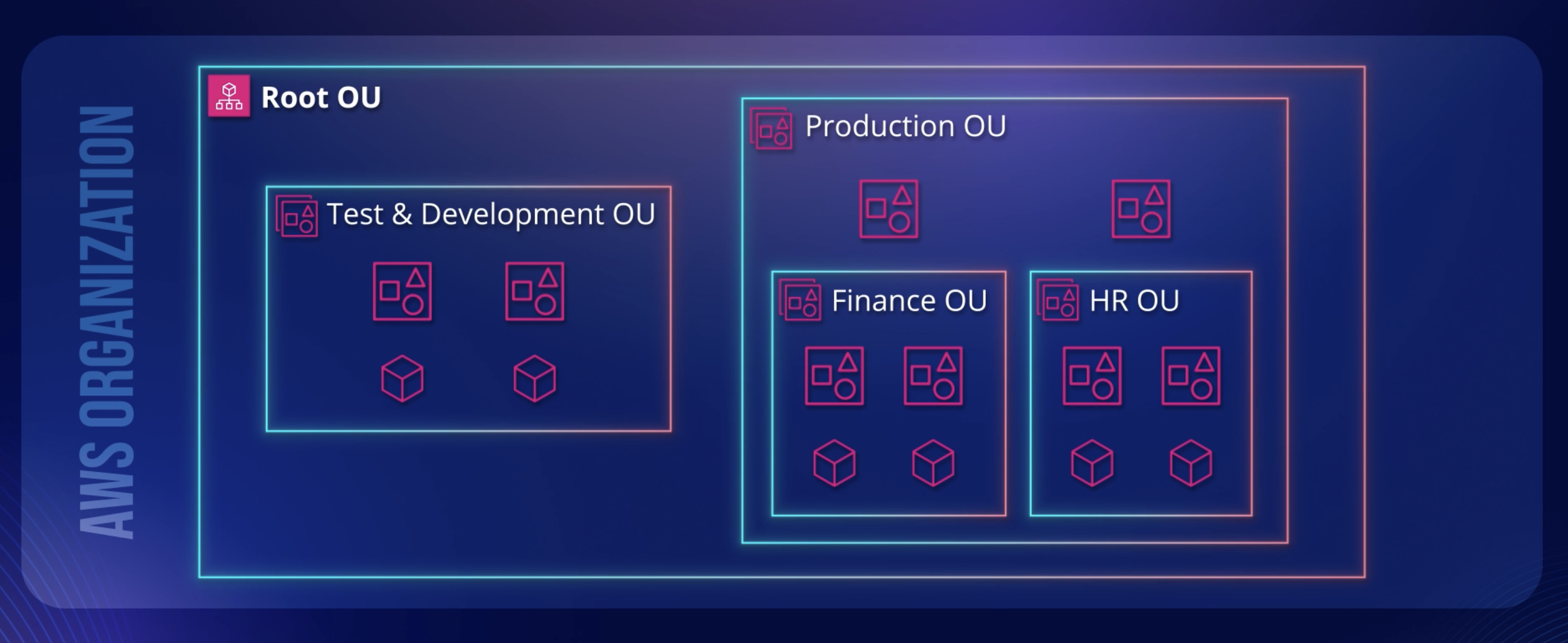
- AWS Orgs used to
centrally managethe AWS account using theOrg Units(OU). - When you create an organization, AWS Organizations automatically creates a root, which is the parent container for all the accounts in your organization.
- You can get one bill per AWS account.
- Here the
star account⭐ is the master account. - Enable/ Disable the services on AWS using the
Service Control Policies(SCP).
Do not use the paying account to deploy the resources.
Root 🌴¶
The parent container for all the accounts for your organization.
Remember!
If you apply an authorization policy to the root, it applies to all organizational units (OUs) and member accounts in the organization but If you apply a management policy to the root, it applies to all organizational units (OUs) and accounts including the management account in the organization.
Organizational Units (OU) 🏛️¶
In AWS Organizations, you can group accounts into OUs to make it easier to manage accounts with similar business or security requirements.
When you apply a policy to an OU, all the accounts in the OU automatically inherit the permissions specified in the policy.
Account 🆔¶
An account in Organizations is a standard AWS account that contains your AWS resources and the identities that can access those resources.
Warning
An AWS account isn't the same thing as a user account. An AWS user is an identity that you create using AWS Identity and Access Management (IAM) and takes the form of either an IAM user with long-term credentials, or an IAM role with short-term credentials. A single AWS account can, and typically does contain many users and roles.
SCP 👮♀️¶
Service control policies (SCPs) are a type of organization policy that you can use to manage permissions in your organization. SCPs offer central control over the maximum available permissions for the IAM users and IAM roles in your organization. SCPs help you to ensure your accounts stay within your organization’s access control guidelines.
SCPs are available only in an organization that has all features enabled. SCPs aren't available if your organization has enabled only the consolidated billing features.
SCP's dont grant permissions and they are just GuardRails💂
SCPs do not grant permissions to the IAM users and IAM roles in your organization. No permissions are granted by an SCP. An SCP defines a permission guardrail, or sets limits, on the actions that the IAM users and IAM roles in your organization can perform.
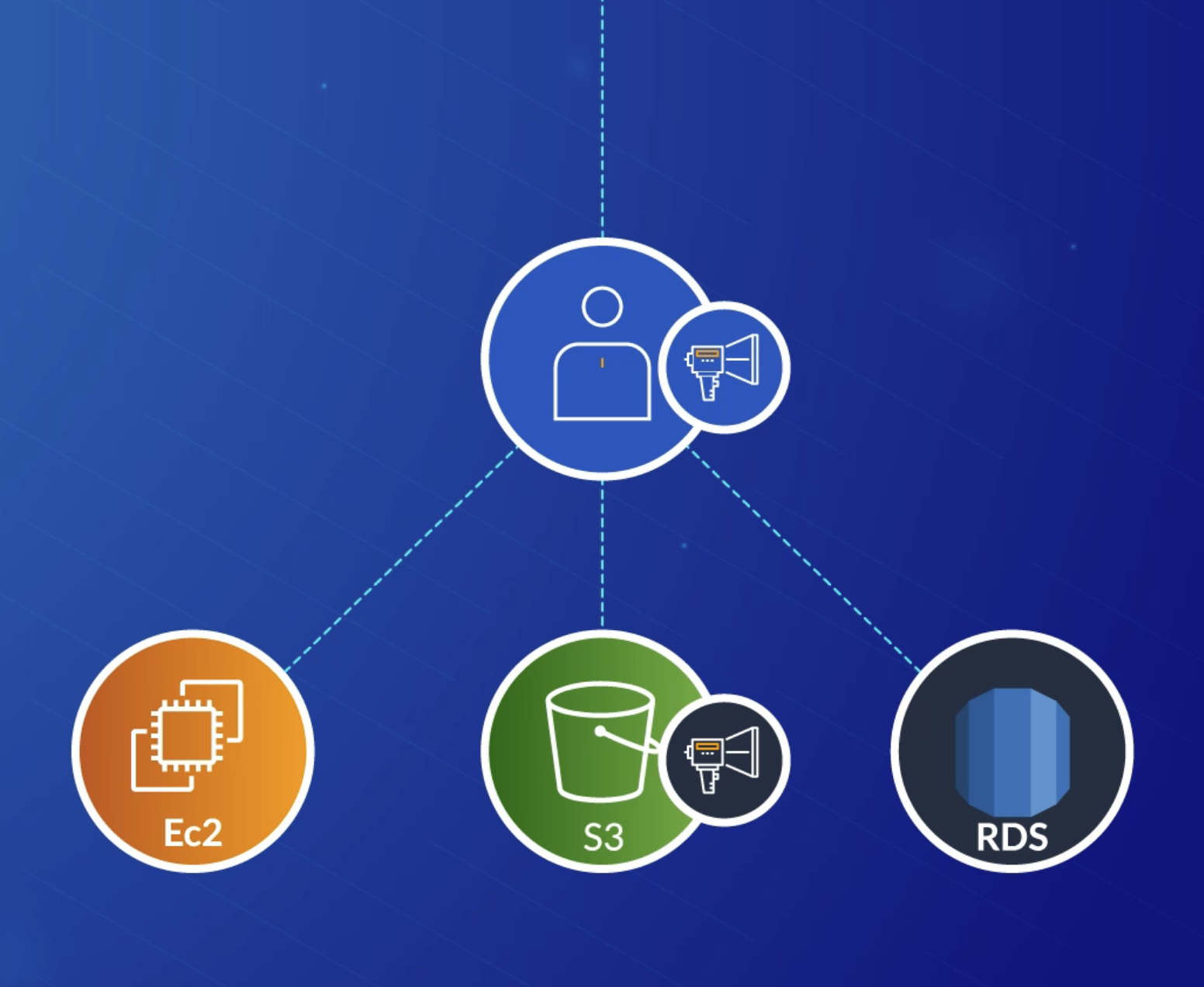
SCP has overriding precedence as shown below (on S3 bucket)