Azure Active Directory ¶
- It is global IAM service for Azure
- We can use it for B2B and B2C (for support)
- We can do monitoring with Azure AD. Example: check if user is logging in from another location based on the distance.
AAD vs Windows server AD
- You must use
Windows Server Active Directoryto update the identity, contact info, or job info for users whose source of authority isWindows Server Active Directory. Usage locationis an Azure property that can only be modified from Azure AD (for all users including Windows Server AD users synced via Azure AD Connect).
AAD Forest¶
As you may know, Active Directory (AD) is a database and set of services that help users get their work done in a Microsoft IT environment. The database (or directory) contains critical information about your environment, including what users and computers there are and who’s allowed to do what. The services control much of the activity that goes on; in particular, they make sure each person is who they claim to be (authentication) and allow them to access only the data they’re allowed to use (authorization).
Active Directory has three main tiers: domains, domain trees and forests:
-
Domainis a group of users, computers and other Active Directory objects that share the sameAD database, such as all the AD objects for your company’s Chicago office. -
Domain treeis a collection of one or multiple domains grouped together in a hierarchical parent-child structure with a contiguous namespace and transitive trust relationships between the domains. For example, the domains Quest.com andSales.Quest.comwould be considered part of theQuest.comdomain tree -
Forestis a group of multiple trees with shared directory schemas, catalogs, application information and domain configurations. The schema defines an object’s class and attributes in a forest, and the global catalog servers provide a listing of all the objects in an AD forest.
Difference between AAD Tenant and AAD Forest
Beyond the structural differences, it’s important to understand the differences in purpose between an Active Directory domain and an Active Directory forest:
-
The domain is a management boundary — The objects for a particular single domain are stored in a single Active Directory database and can be managed together.
-
The forest is a security boundary — Objects in different Active Directory forests are not able to interact with each other unless the administrators of each forest create a trust between them.
Security basics¶
User Principal: The one accessing the accountService Principal: Identity created by system to access applicationsAudience: The Audince is the applicaton id for API which your App has permissions on-
Role and Scope: Scopes are typically associated with API access. An API defines what scopes are available (what services it provides). For example a user account management API might define scopes likeread:user, create:user, update:user. These are the capabilities the API provides, but not necessarily what any given user can do.In the “Role & Scope” model, Roles are defined, and users are given a Role. Individual Scopes are associated with a given Role, combining all these elements together. For example, you might have:
Role: Audit, API: user_manager, Scopes: read:user Role: Access Control, API: user_manager, Scopes: create:user, update:userAnd maybe Amar has the Audit role, while Bob has the Access Control role.
When you request a scope, the Authorization Server (Auth0/AAD) will decide whether you get that scope or not. You can request anything you like, but the
Authorization Serversends back a token with only the scopes it has decided you are allowed to have.Role defination example{ "value": [ { "properties": { "roleName": "Billing Reader Plus", "type": "CustomRole", "description": "Read billing data and download invoices", "assignableScopes": [ "/subscriptions/{subscriptionId1}" ], "permissions": [ { "actions": [ "Microsoft.Authorization/*/read", "Microsoft.Billing/*/read", "Microsoft.Commerce/*/read", "Microsoft.Consumption/*/read", "Microsoft.Management/managementGroups/read", "Microsoft.CostManagement/*/read", "Microsoft.Billing/invoices/download/action", "Microsoft.CostManagement/exports/*" ], "notActions": [ "Microsoft.CostManagement/exports/delete" ], "dataActions": [], "notDataActions": [] } ], "createdOn": "2021-05-22T21:57:23.5764138Z", "updatedOn": "2021-05-22T21:57:23.5764138Z", "createdBy": "{createdByObjectId1}", "updatedBy": "{updatedByObjectId1}" }, "id": "/subscriptions/{subscriptionId1}/providers/Microsoft.Authorization/roleDefinitions/{roleDefinitionId1}", "type": "Microsoft.Authorization/roleDefinitions", "name": "{roleDefinitionId1}" } ] }
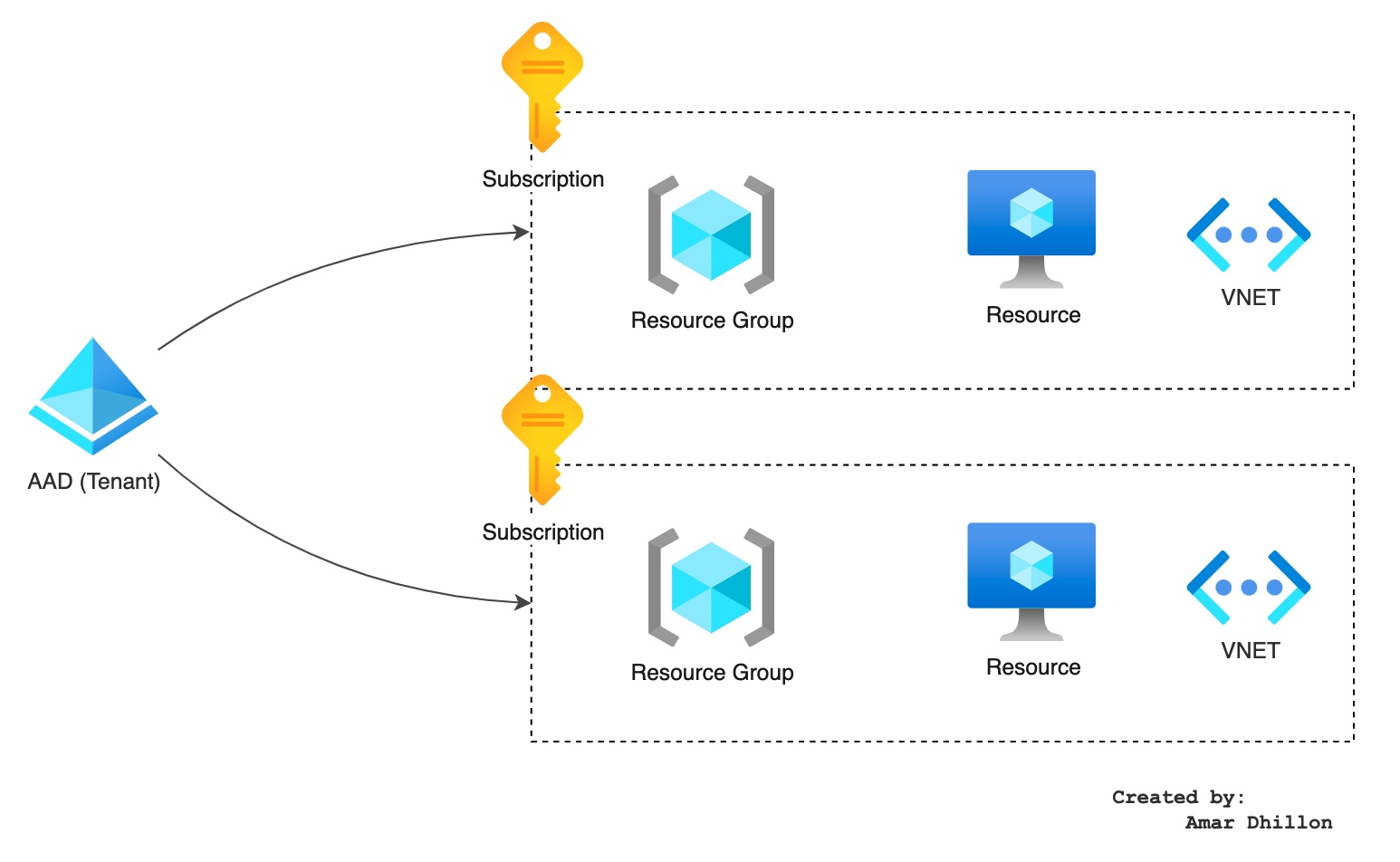
What is Azure AD tenant?¶
Tldr
Tenant is an instance of AAD
An Azure AD tenant is a reserved Azure AD service instance that an organization receives and owns once it signs up for a Microsoft cloud service such as Azure, Microsoft Intune, or Microsoft 365.
Remember
Each tenant represents an organization, and is distinct and separate from other Azure AD tenants.
SCP (Service Connection Point)¶
The Active Directory Schema defines a Service Connection Point (SCP) object class to make it easy for a service to publish service-specific data in the directory. Clients of the service use the data in an SCP to locate, connect to, and authenticate an instance of your service.
Service Principal¶
An Azure service principal is an identity created for use with applications, hosted services, and automated tools to access Azure resources. This access is restricted by the roles assigned to the service principal, giving you control over which resources can be accessed and at which level.

For security reasons, it's always recommended to use service principals with automated tools rather than allowing them to log in with a user identity.
There are two types of authentication available for service principals:
- Password-based authentication
- Certificate-based authentication.
SP VS Managed Identity¶
SP and Managed Identity
The difference between managed identities and service principals is subtle. Service principals are no longer recommended for services that support managed identities. Managed identities are effectively “managed service principals” and remove the need for storing credentials in the application’s configuration and instead inject certificates into the resource that the managed identity is created into.
Active Directory vs Azure AD¶
They are not competing services. Think of them as 2 separate services.
| Acrive Directory | Azure AD |
|---|---|
| Organizational Units | Administrative Units |
| Kerberos, LDAP | SAML, OAuth |
| Hierarchial | Flat structure |
| On Premise | Cloud based and Global |
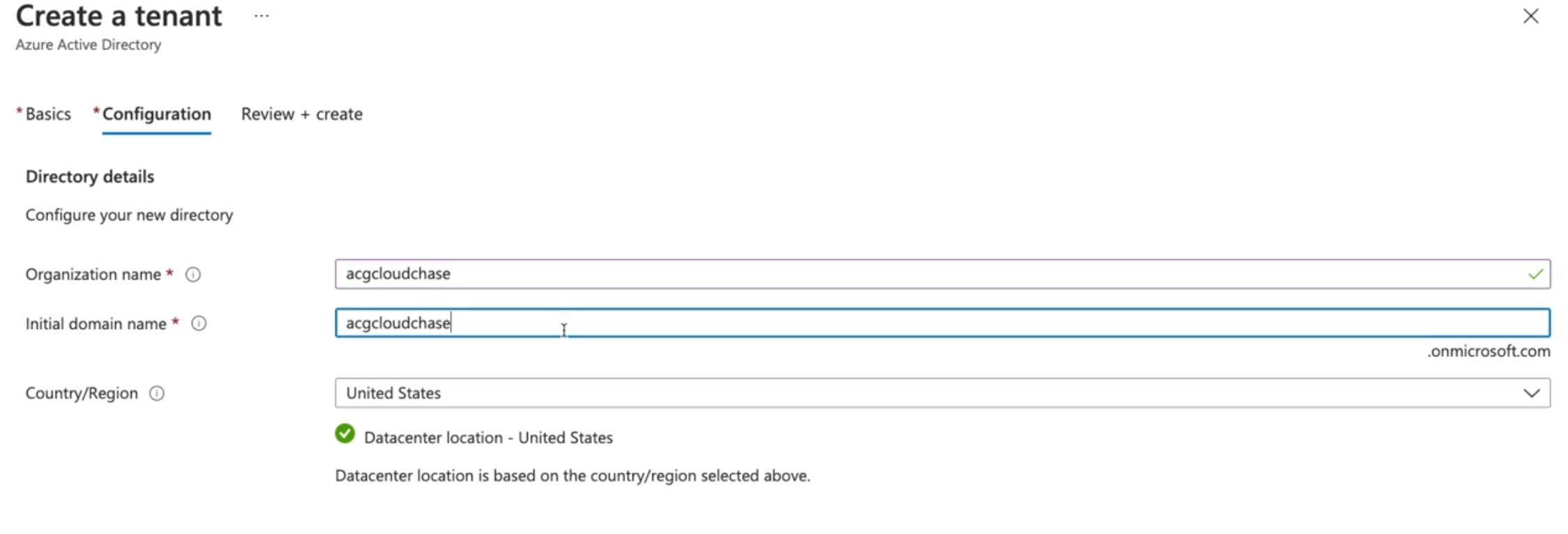
Default Tenant¶
The default tenant is created when we create first subscription. Later, we can create another tenant and will have option to switch between various tenants. Below you can see how we can create a new tenant.
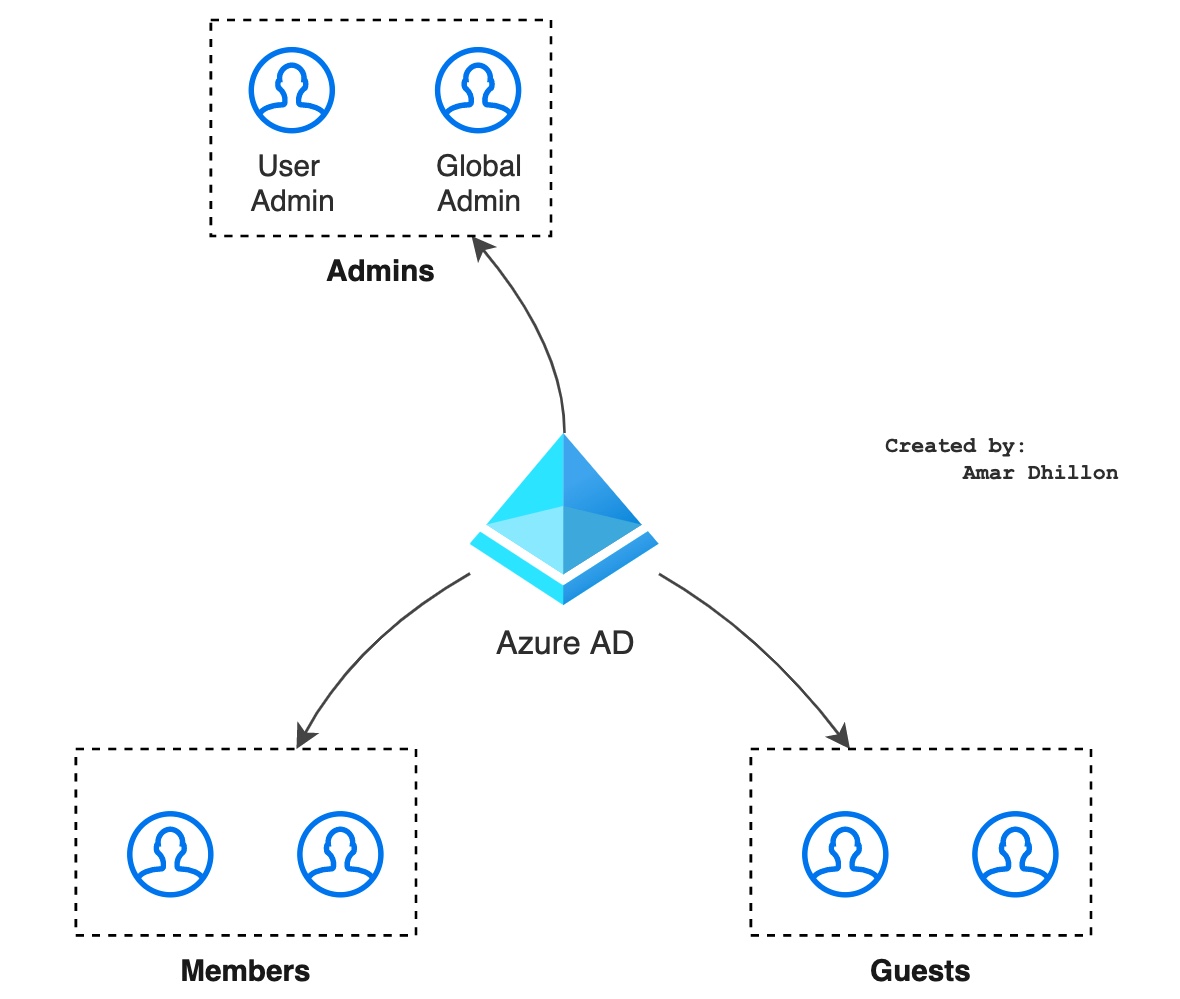
Users¶
- Users are set of JSON properties
Types of users:
- Admins
- Members:
Assigned: Specifically assign a user to a groupDynamic user: Rules are created which automate group membership via user attributes- Guests
Communication bw diff tenants¶
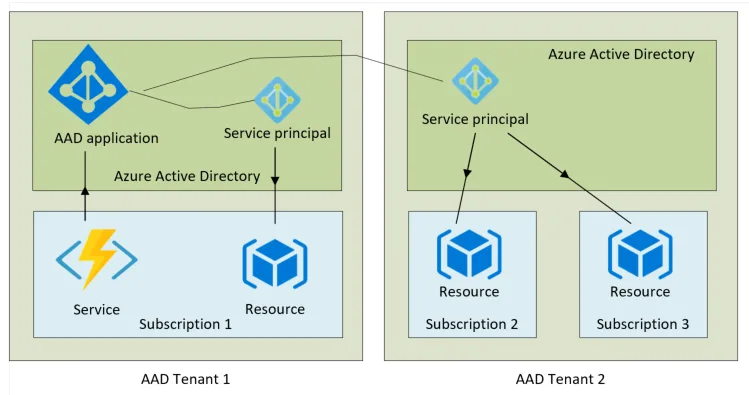
The associated service principal in tenant 1 will be used to authenticate to resources within the service's own subscription. A separate associated service principal which resides in tenant 2 will be used to authenticate to resources in subscriptions 2 and 3.
Core Concepts¶
Groups¶
Type of groups:
- Security Group: Azure AD Security Groups are analogous to Security Groups in on-prem Windows Active Directory. They are Security Principals, which means they can be used to secure objects in Azure AD. They can be created natively in Azure AD, or synced from Windows AD with Azure AD Connect. Their membership can be static, or it can be generated dynamically with rules.
- Microsoft 365: Microsoft 365 Groups are a membership object in Microsoft 365 that eases the task of ensuring a group of people have consistent permissions to a group of related resources. You may see them referred to as Microsoft 365 Groups or Unified Groups.
Dynamic groups¶
Dynamic group membership adds and removes group members automatically using membership rules based on member attributes. You can set up a rule for dynamic membership on security groups or Microsoft 365 groups.
Remember
When the attributes of a user or a device change, the system evaluates all dynamic group rules in a directory to see if the change would trigger any group adds or removes. If a user or device satisfies a rule on a group, they're added as a member of that group. If they no longer satisfy the rule, they're removed. You can't manually add or remove a member of a dynamic group.
Rule Builder¶
Azure AD provides a rule builder to create and update your important rules more quickly. The rule builder supports the construction of up to five expressions. The rule builder makes it easier to form a rule with a few simple expressions, however, it can't be used to reproduce every rule. If the rule builder doesn't support the rule you want to create, you can use the text box.
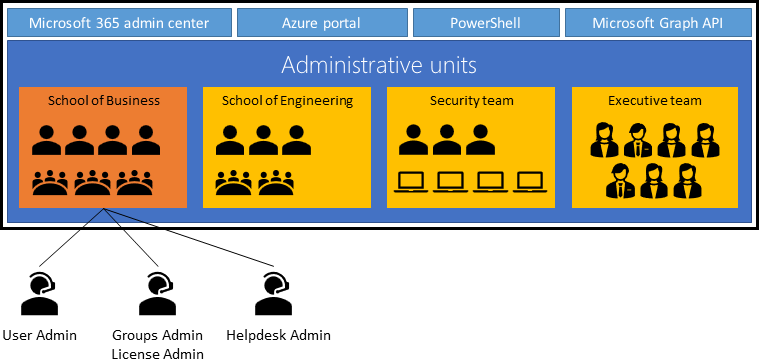
Administrative Units¶
An administrative unit is an Azure AD resource that can be a container for other Azure AD resources. An administrative unit can contain only users, groups, or devices.
Use of Admin Units
Administrative units restrict permissions in a role to any portion of your organization that you define. You could, for example, use administrative units to delegate the Helpdesk Administrator role to regional support specialists, so they can manage users only in the region that they support.
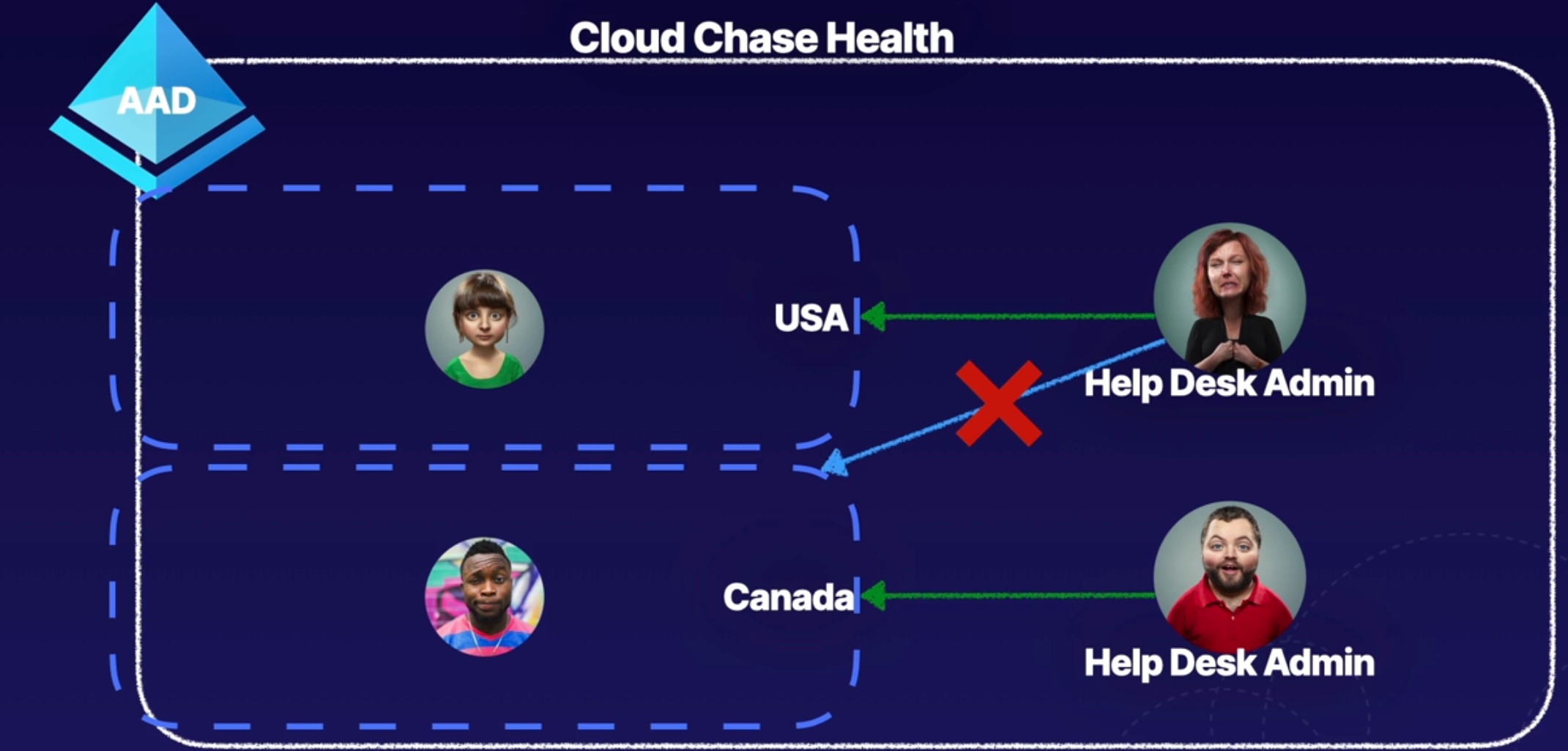
A use case scenario
It can be useful to restrict administrative scope by using administrative units in organizations that are made up of independent divisions of any kind. Consider the example of a large university that's made up of many autonomous schools (School of Business, School of Engineering, and so on). Each school has a team of IT admins who control access, manage users, and set policies for their school.
A central administrator could:
- Create an AU for the School of Business.
- Populate the AU with only students and staff within the School of Business.
- Create a role with administrative permissions over only Azure AD users in the School of Business AU.
- Add the business school IT team to the role, along with its scope.
AAD Connect¶
Azure AD Connect is an on-premises Microsoft application that's designed to meet and accomplish your hybrid identity goals. If you're evaluating how to best meet your goals, you should also consider the cloud-managed solution Azure AD Connect cloud sync.
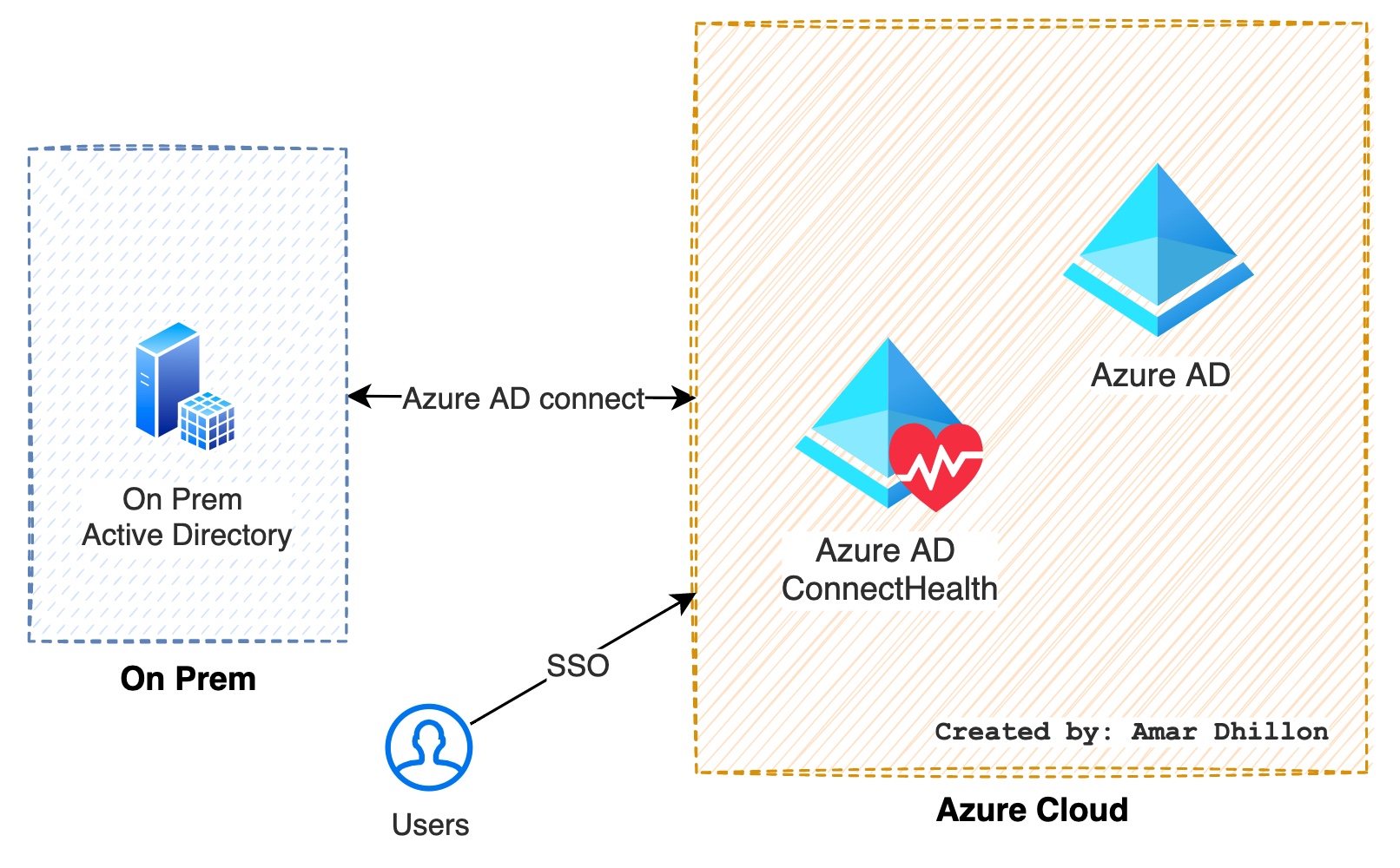
What is AAD Connect Health?
Azure Active Directory (Azure AD) Connect Health provides robust monitoring of your on-premises identity infrastructure. It enables you to maintain a reliable connection to Microsoft 365 and Microsoft Online Services.
Azure AD Connect sync¶
Azure AD Connect sync synchronize changes occurring in your on-premises directory using a scheduler. There are two scheduler processes:
- one for password sync
- another for object/attribute sync and maintenance tasks
When to Sync?
By default every 30 minutes a synchronization cycle is run. If you have modified the synchronization cycle you will need to make sure that a synchronization cycle is run at least once every 7 days.
Tip
Best way is either a Synchronization being executed through the Azure AD Connect, in the Portal or using the command Start-ADSyncSyncCycle -PolicyType Delta. Running a full sync cycle can be very time-consuming, so if you need to replicate the user information to Azure AD immediately then run Start-ADSyncSyncCycle -PolicyType Delta.
Licence¶
Many AAD services require you to license each of your users or groups (and associated members) for that service. Only users with active licenses will be able to access and use the licensed Azure AD services for which that's true. Licenses are applied per tenant and don't transfer to other tenants.
Configuring SSPR (Self Service Password Reset)¶
Azure Active Directory (Azure AD) self-service password reset (SSPR) gives users the ability to change or reset their password, with no administrator or help desk involvement. If Azure AD locks a user's account, or they forget their password, they can follow prompts to unblock themselves and get back to work. This ability reduces help desk calls and loss of productivity when a user can't sign in to their device or an application.
SSPR can be set for
- All users
- None
- Selected Users
Remember
- Security questions as an authentication method is not available for admins
- Admins are always enabled for SSPR and need to have 2 security methods to reset their password.
Various options for SSPR are
- Mobile app notification
- Mobile app code
- Mobile phone call
- Office phone call
- Security questions (least recommended)
Device Management¶
- We can register the devices which are not in our organization
Azure AD registered devices are signed in to using a local account like a Microsoft account on a Windows 10 or newer device. These devices have an Azure AD account for access to organizational resources. Access to resources in the organization can be limited based on that Azure AD account and Conditional Access policies applied to the device identity.
MDM
Administrators can secure and further control these Azure AD registered devices using Mobile Device Management (MDM) tools like Microsoft Intune. MDM provides a means to enforce organization-required configurations like requiring storage to be encrypted, password complexity, and security software kept updated.
Registration options¶
We have 3 options: - Azure AD registered: This is the least restrictive and allows BYOD. Also supportgs iOS and macOS - Azure AD joined: Azure AD joined devices are signed in to using an organizational Azure AD account. In this case the device is owned by organization. - Hybrid Azure AD joined: Joined to on-premises AD and Azure AD requiring organizational account to sign in to the device
Conditional Access Policy¶
Info
Organizations who have deployed Microsoft Intune can use the information returned from their devices to identify devices that meet compliance requirements such as:
Requiring a PIN to unlock
Requiring device encryption
Requiring a minimum or maximum operating system version
Requiring a device isn't jailbroken or rooted
RBAC and AAD roles¶
Roles have descending effect as shown in below figure
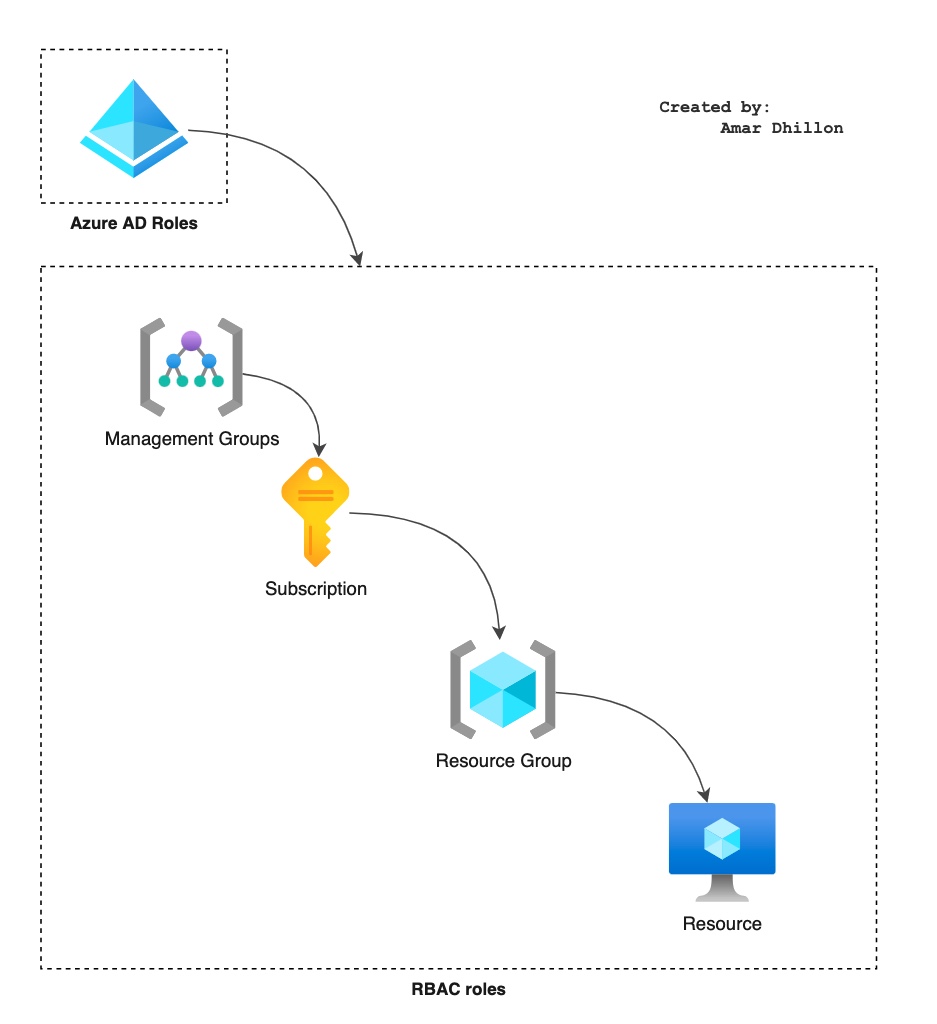
RBAC Vs Azure AD?
Azure (RBAC) and Azure AD roles are independent. AD roles do not grant access to resources and Azure roles do not grant access to Azure AD. However, a Global Administrator in AD can elevate access to all subscriptions and will be User Access Administrator in Azure root scope.
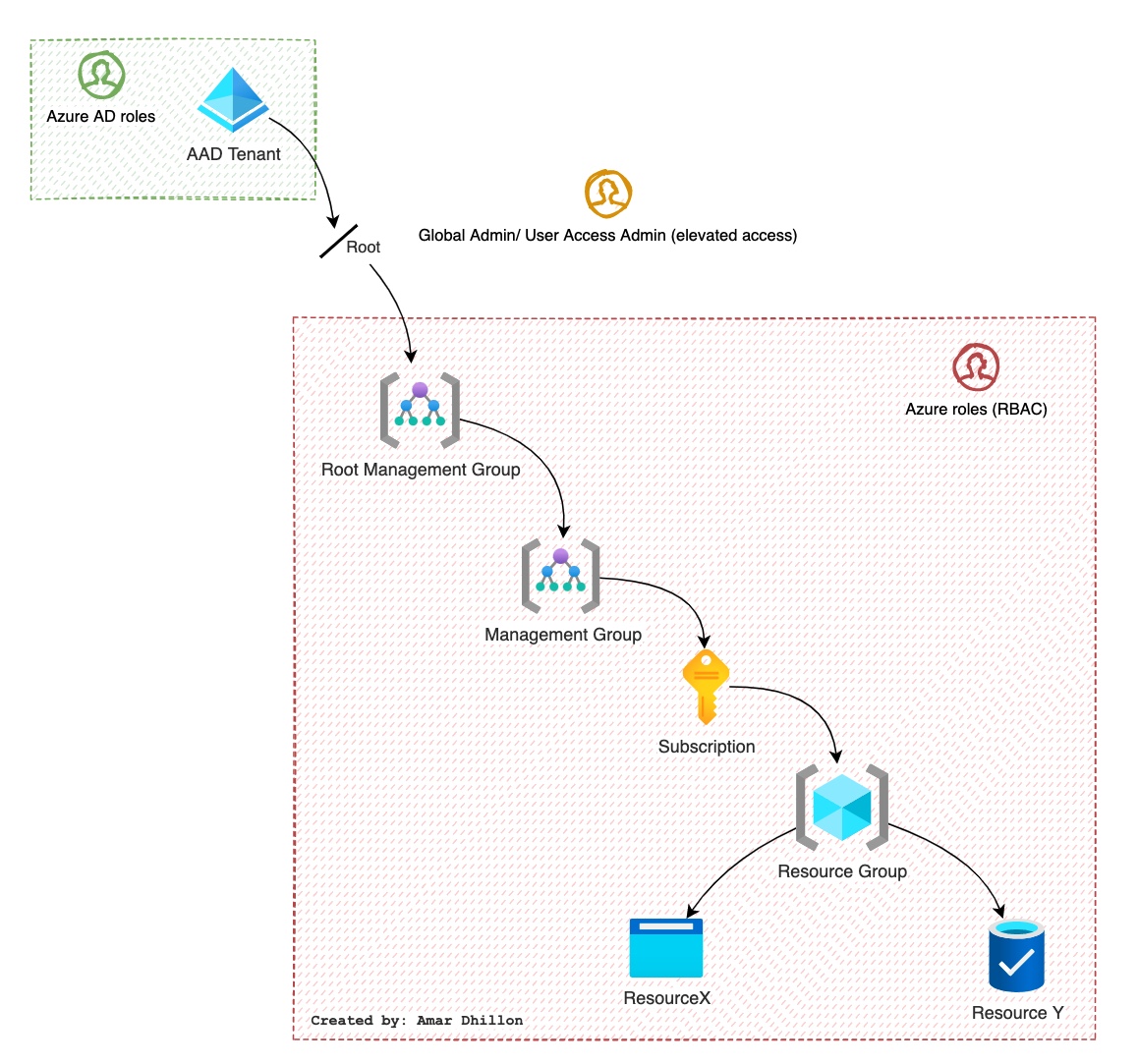
Elevated access for global admin¶
When you set the toggle to Yes, you are assigned the User Access Administrator role in Azure RBAC at root scope /. This grants you permission to assign roles in all Azure subscriptions and management groups associated with this Azure AD directory. This toggle is only available to users who are assigned the Global Administrator role in Azure AD.
When you set the toggle to No, the User Access Administrator role in Azure RBAC is removed from your user account. You can no longer assign roles in all Azure subscriptions and management groups that are associated with this Azure AD directory. You can view and manage only the Azure subscriptions and management groups to which you have been granted access.
Azure RBAC roles¶
Owner: Grants full access to manage all resources, including the ability to assign roles in Azure RBAC.Contributor: Grants full access to manage all resources, but does NOT allow you to assign roles in Azure RBAC. (you cannot add users or changes their rights)User Access Administrator: Lets you manage user access to Azure resources.Reader: View all resources, but does not allow you to make any changes.Security Admin: View and update permissions for Security Center. Same permissions as the Security Reader role and can also update the security policy and dismiss alerts and recommendations.Network Contributor: Lets you manage networks, but not access to them. (so you can add VNET, subnet, etc)
Azure AD roles¶
Global admin role: Can manage azure AD resourcesBilling admin role: Can perform billing tasksUser admin role: Can manage users and groupsHelpdesk admin: Can reset passwords
Scope of roles
Scope of AD roles is at tenant level whereas RBAC roles scope can be at different levels
MFA Provider¶
Info
Authentication providers can be found in the Azure portal > Azure Active Directory > Security > MFA > Providers
Two-step verification is available by default for Global Administrators who have Azure Active Directory, and Microsoft 365 users. However, if you wish to take advantage of advanced features then you should purchase the full version of Azure AD Multi-Factor Authentication (MFA).
An Azure AD Multi-Factor Auth Provider is used to take advantage of features provided by Azure AD Multi-Factor Authentication for users who do not have licenses.
Warning
You can't change the usage model (per enabled user or per authentication) after an MFA provider is created.
Per-user¶
The per-user option calculates the number of users who are eligible to perform MFA, which is all users in Azure AD, and all enabled users in MFA Server. This option is best if some users have licenses, but you need to extend MFA to more users beyond your licensing limits.
Per authentication¶
The per-authentication option calculates the number of authentications performed against your tenant in a month. This option is best if some users authenticate only occasionally
3rd party access¶
Catalog¶
A catalog is a container of resources and access packages. You create a catalog when you want to group related resources and access packages. An administrator can create a catalog
Create a new catalog using Azure Active Directory --> Identity Governance
Access package¶
An access package enables you to do a one-time setup of resources and policies that automatically administers access for the life of the access package
All access packages must be put in a container called a catalog. A catalog defines what resources you can add to your access package. If you don't specify a catalog, your access package will be put into the general catalog. Currently, you can't move an existing access package to a different catalog.
Access package assignments¶
In entitlement management, you can see who has been assigned to access packages, their policy, and status.
Application Proxy¶
Application Proxy is a feature of Azure AD that enables users to access on-premises web applications from a remote client. Application Proxy includes both the Application Proxy service which runs in the cloud, and the Application Proxy connector which runs on an on-premises server. Azure AD, the Application Proxy service, and the Application Proxy connector work together to securely pass the user sign-on token from Azure AD to the web application.
Access reviews¶
Access reviews in Azure Active Directory (Azure AD), part of Microsoft Entra, enable organizations to efficiently manage group memberships, access to enterprise applications, and role assignments. User's access can be reviewed regularly to make sure only the right people have continued access.
Why are access reviews important?
Azure AD enables you to collaborate with users from inside your organization and with external users. Users can join groups, invite guests, connect to cloud apps, and work remotely from their work or personal devices. The convenience of using self-service has led to a need for better access management capabilities.
- As new employees join, how do you ensure they have the access they need to be productive?
- As people move teams or leave the company, how do you make sure that their old access is removed?
- Excessive access rights can lead to compromises.
- Excessive access right may also lead audit findings as they indicate a lack of control over access.
- You have to proactively engage with resource owners to ensure they regularly review who has access to their resources.
Privileged Identity Management¶
Privileged Identity Management provides time-based and approval-based role activation to mitigate the risks of excessive, unnecessary, or misused access permissions on resources that you care about. Here are some of the key features of Privileged Identity Management:
- Provide
just-in-time privileged accessto Azure AD and Azure resources - Assign time-bound access to resources using start and end dates
- Require approval to activate privileged roles
- Enforce multi-factor authentication to activate any role
- Use justification to understand why users activate
- Get notifications when privileged roles are activated
- Conduct access reviews to ensure users still need roles
- Download audit history for internal or external audit
- Prevents removal of the last active Global Administrator and Privileged Role Administrator role assignments